In-brief: Encryption keys used to secure data on- and communications between embedded devices are being recycled, creating a huge vulnerability that malicious hackers could exploit to snoop on sensitive communications or impersonate devices.
OpenSSL Foundation
VENOM Vulnerability Renews Shared Code Worries
In-brief: The recently disclosed VENOM vulnerability dispels the myth that virtual machines are immune to cyber attacks, and raises important questions about our reliance on shared code.
OpenSSL Issuing Fixes for High Severity Flaws on Thursday
In-brief: The OpenSSL Project is publishing software updates to address a range of security flaws, at least one of them rated “critical.” The update comes amid a comprehensive audit of the OpenSSL code.
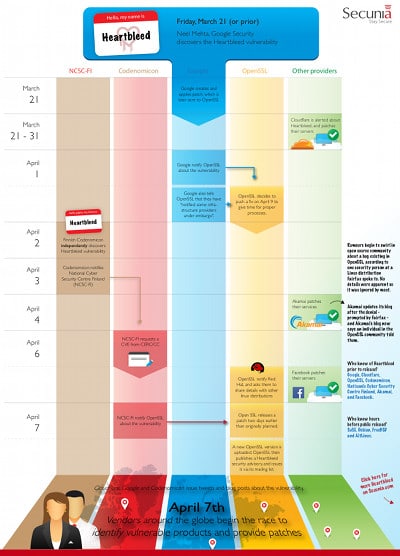
Infographic: A Heartbleed Disclosure Timeline (Secunia)
The dangerous security hole in OpenSSL known as “Heartbleed” has (mostly) faded from the headlines, but that doesn’t mean it isn’t still dangerous. As this blog has noted, the Heartbleed vulnerability was patched quickly on major platforms like Apache and nginx and by high profile service providers like Google and Facebook. But it still has a long tail of web applications that aren’t high risk (i.e. directly reachable via the Internet) and embedded devices that use OpenSSL or its various components. As the folks over at Acunetix note in a blog post today, hundreds of other services, application software and operating systems make use of OpenSSL for purposes that might be entirely unrelated to delivering pages over HTTPS. This includes all the email servers (using SMTP, POP and IMAP protocols), FTP servers, chat servers (XMPP protocol), virtual private networks (SSL VPNs), and network appliances that use OpenSSL or its components. The number of systems vulnerable to […]
Heart Attack? Fixes For More Critical Holes In OpenSSL
Just a month after a critical security hole in OpenSSL dubbed “Heartbleed” captured headlines around the globe, The OpenSSL Foundation has issued an other critical software update fixing six more security holes, two of them critical. The Foundation issued its update on Thursday, saying that current versions of OpenSSL contain vulnerabilities that could be used to carry out “man in the middle” (or MITM) attacks against OpenSSL clients and servers. SSL VPN (virtual private network) products are believed to be especially vulnerable. Users of OpenSSL versions 0.9.8, 1.0.0 and 1.0.1 are all advised to update immediately. According to information released by the OpenSSL Foundation, an attacker using a carefully crafted handshake can force the use of “weak keying material in OpenSSL SSL/TLS clients and servers.” That could lay the groundwork for man-in-the-middle attacks in which an attacker positions herself between a vulnerable client and server, decrypting and modifying traffic as it passes through the attacker’s […]