Despite a litany of high-profile data breaches, federal action on data privacy is unlikely to go anywhere in 2019 as partisanship and lack of technology literacy complicate Congressional action.
Facebook opens up on System that ‘protects Billions’
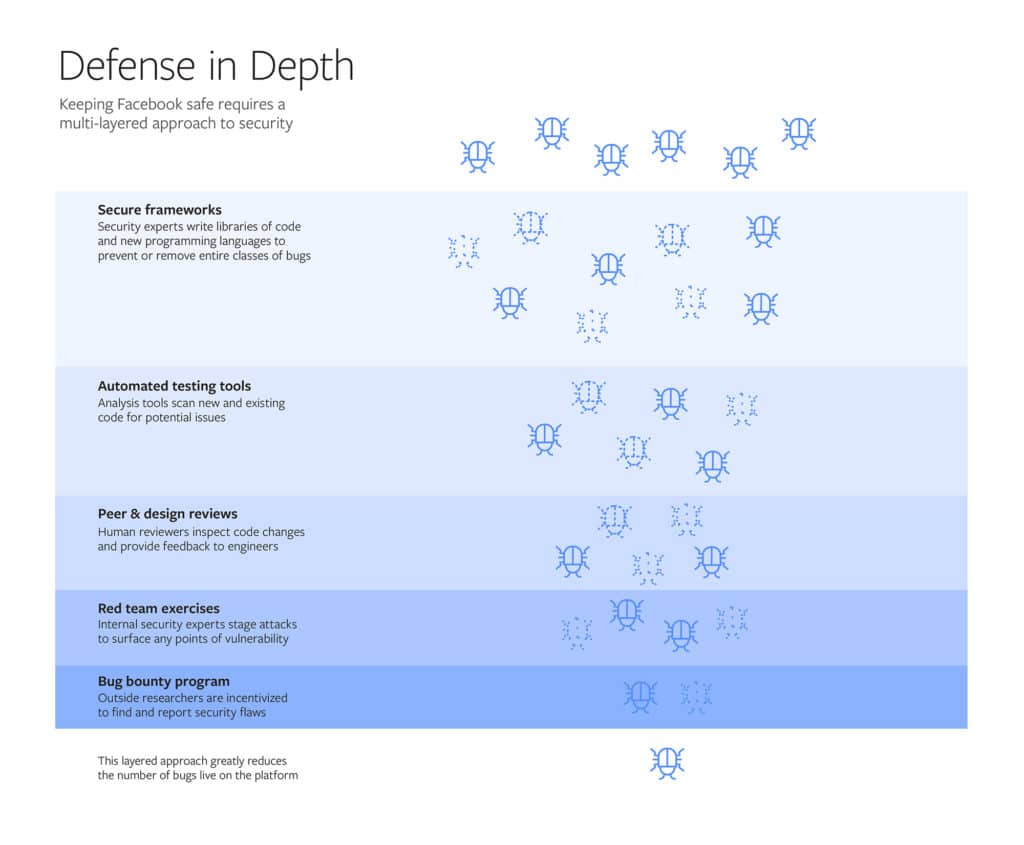
Facebook used a blog post on Friday to describe, in detail, the systems that it uses to secure its vast social network, including custom designed tools and so-called “red team” hacks.
Facebook: We Didn’t Give Anyone Data Without User Permission
Facebook’s terrible, horrible, no good, very bad year continued, with the social media company on the defense yet again over partnerships that granted high-tech companies extensive access to user data.
Episode 124: The Twitter Accounts Pushing French Protests. Also: social engineering the Software Supply Chain
In this week’s podcast (#124): we speak with French security researcher Baptiste Robert about research on the social media accounts pushing the french “Yellow Vest” protests. Surprise, surprise: they’re not french. Also: Brian Fox of the firm Sonatype joins us to talk about the recent compromise of the Github event-stream project and why social engineering poses a real risk to the security of the software supply chain.
Episode 114: Complexity at Root of Facebook Breach and LoJax is a RAT You Can’t Kill
In this week’s podcast: Facebook revealed that a breach affected 50 million accounts and as many as 90 million users. Is complexity at the root of the social media giant’s troubles? We speak with Gary McGraw of the firm Synopsys about it. Also: BIOS-based malware has been demonstrated at security conferences for years. Last week, the security firm ESET warned that it identified a sample in the wild. Even worse: the Russian Hacking Group Fancy Bear was believed to be responsible. We’ll talk to firmware security expert Giovanni Vigna of the firm Lastline about the truth and hype around LoJax and other firmware based attacks.