In-brief: a survey of key sectors found that energy and utilities firms are struggling to reduce their risk of an attack.
BitSight
Infographic: After A Year of Breaches, Are Retailers More Secure?
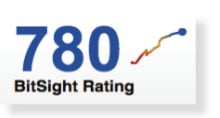
After a year in which some of the U.S.’s top retailers found themselves on the wrong side of sophisticated, cyber criminal hacking groups, you may be tempted to search for a silver lining. Maybe the up side of all the attacks on retail networks and point of sale systems is an improved security posture overall? After all: if your neighbors to the left and right have their house broken into, you may well beef up your locks and alarms, even if your house hasn’t been targeted. Or, at least, that’s how the thinking goes. But Boston-based BitSight took a look at how the retail sector is faring security-wise as 2014 draws to a close. BitSight is an interesting company. They market a kind of reputation monitoring service: assessing security posture for companies by observing how they look from the outside. Think of it as a kind of Experian or TransUnion for security. […]
Supply Chain Transparency Doesn’t Extend To Security
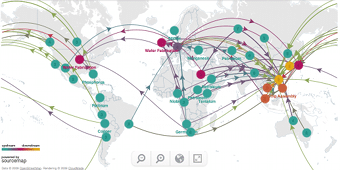
We live in an ever-more unstable world in which massive disruptions, whether natural or man-made, are a frequent occurrence. Companies that make everything from aircraft to mobile phones to cappuccino need to be nimble – sidestepping global calamities that might idle assembly lines or leave customers without their morning cup of coffee. As in other areas, the benefits of technology advancements like cheap, cloud based computing, remote sensors and mobility are transforming the way that companies manage their vast, global network of suppliers. These days, supply chain transparency is all the rage – allowing companies to share information seamlessly and in realtime with their downstream business partners and suppliers. Firms like the start-ups Sourcemap, and LlamaSoft are offering “supply chain visualization” technology that leverages a familiar formula these days: mobility, social networking, crowd-sourced intelligence, and “Big Data” analytics. [There’s more to read about supply chain security on The Security Ledger.] However, as […]
BitSight: A Equifax For Security Risk?
I’ve opined in these pages and elsewhere that one of the big problems in the IT security space is the absence of actionable data. After all, problems like denial of service attacks, network compromises and inadvertent data leaks are all just risks that organizations and individuals must grapple with in our increasingly wired world. True – they’re new kinds of risks, but otherwise they’re not fundamentally different from problems like auto accidents, property crime or illness – things that we do a good job accounting for. The difference, as I see it, is an absence of accepted and independent means of assessing the relative security posture of any organization. IT security is still so much dark magic: we rely on organizations to tell us about how secure they are. Organizations, in turn, rely on a complex and patchy network of security monitoring and detection tools, then try to read the […]