Polls and surveys are of limited use in telling us exactly what people are thinking or how they’ll act. This is a lesson we (re) learn every four years, when political junkies ride the “message” of each new poll, only to get schooled by voters on election day for over-reading the results of individual polls or failing to notice obvious flaws with the way in which the poll or survey was conducted – or who (or what) was behind the poll.
But the other thing we constantly have to (re)learn is that, while individual polls and surveys are a poor way to understand what’s going on, consistent patterns that span multiple polls over time often prove accurate and are borne out by events.
That’s why I look a recent spate of surveys that attempt to measure awareness of software supply chain risks as so interesting. While they differ in methodology and focus, these surveys present a clear message. Namely: threats and risks from vulnerable software supply chain are real, and they’re starting to freak people out.
Report: Digital Supply Chain Breaches Impact 98% of Organizations
GitGuardian: security practitioners worried about secrets leaks
The latest example of this is are findings from a newly released survey sponsored by GitGuardian. The survey of what GitGuardian describes as ”507 IT and security decision-makers” sought to gauge awareness about the risks posed by development secrets sprawl in large enterprises. Their conclusion? Development secrets leaks are a real problem and a major source of cyber risk for organizations. In fact, three quarters (75%) of those responding to the GitGuardian survey said that their organization had experienced a secret leak. Fully 60% said a secret leak occurred that affected the company or its employees.
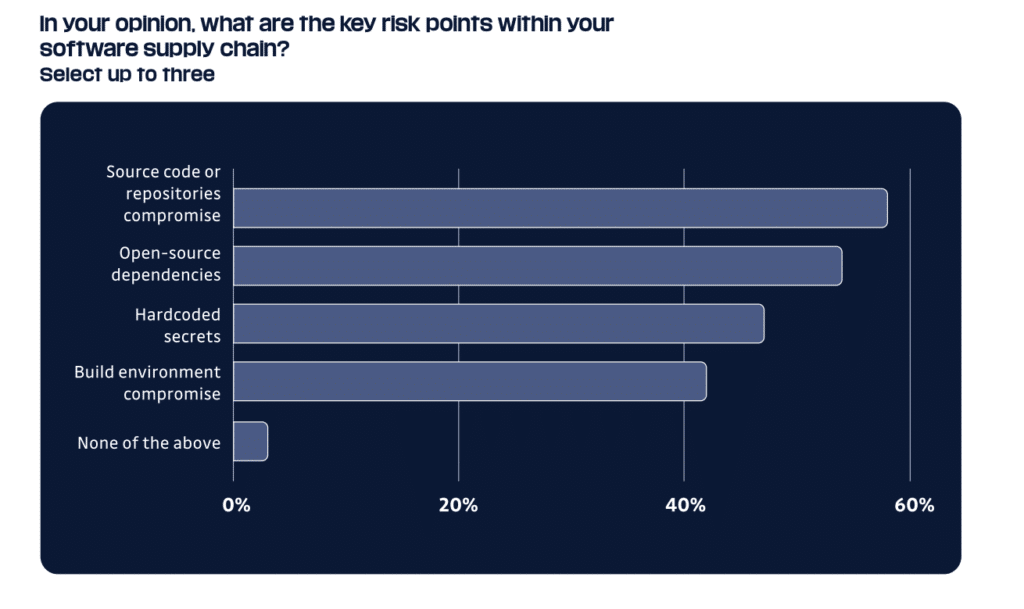
The study, “Voice of Practitioners: The State of Secrets in AppSec” (PDF) was conducted for GitGuardian by Sapio research. Vulnerable code was, by and large, the cause of those leaks. Almost two thirds of respondents (58%) said that “source code” or compromise of repositories was the “key risk point” in their software supply chain. More than half said that open source dependencies were a key risk point.
Lax operational practices also play a role. When asked by GitGuardian “How do your development teams share passwords and secrets when building applications today?”, 30% of the respondents said, “They share them in plaintext through messaging apps.” Yikes!
Despite that, the IT and security decision makers admitted that their organization had only imperfect methods for addressing software supply chain risk. More than a quarter (27%) said their organization still relies on manual code reviews to detect hard coded secrets. Less than a quarter (17%) said they used a secrets manager to eliminate the need to embed secrets in code, GitGuardian reported.
ReversingLabs survey finds supply chain risks growing
Of course, that’s just one survey. But its findings line up with other, recent polls of IT pros, developers and cybersecurity experts. Notably, a survey by Dimensional Research for ReversingLabs last month contained similar warnings. (Note: please read about my work with ReversingLabs here.)
The ReversingLabs Software Supply Chain Risk Survey polled executives and IT professionals responsible for software at enterprise-scale companies. In that poll, also, the IT pros professed deep concerns about the impact of software supply chain risks. Eighty-eight percent of respondents in the ReversingLabs survey said software supply chain security presented an “enterprise-wide risk” to their organizations, while nearly two thirds (65%) said their organizations’ software supply chain security program wasn’t as mature as it should be.

And, as with the GitGuardian survey, supply chain risks and leaked development secrets loomed large in the minds of the surveyed IT and security professionals. Asked what issues pose the biggest business risk to their organizations, 55% said the exposure of secrets such as sensitive information, access tokens and credentials in software code, followed by secrets in malicious code (52%), and suspicious code (46%) that had been inserted into applications.
Asus ShadowHammer suggests Supply Chain Hacks are the New Normal
Of course, vulnerable software is still the biggest perceived threat amongst IT pros. Fully 82% of respondents cited software containing vulnerabilities as their biggest business risk. And software vulnerabilities in code were the most common issue survey takers reported, with 65% having encountered them in the last 12 months, the Dimensional survey for ReversingLabs found. But supply chain related threats are also getting bigger on IT pros’ radars. Those surveyed by ReversingLabs cited certificate misconfigurations (37%), exposed secrets (25%) and suspicious code (24%) as common issues they encounter.
Wanted: big, structural changes
What is the fix for growing supply chain threats (and the resultant anxiety among IT and security pros)? Software manufacturers have to start prioritizing security and focusing on common problems like secrets leak. Alas, there’s not much evidence that is happening. The GitGuardian survey, for example, found that investment in secrets leak detection was still a low priority for organizations despite the clear recognition of the risk posed by leaked development secrets.
Episode 218: Denial of Sustenance Attacks -The Cyber Risk To Agriculture
Big, structural changes are needed to raise the level of application security. The U.S. government has been promoting its “secure by design and default” guidance promoted by CISA, the Cybersecurity and Infrastructure Security Agency, in collaboration with the FBI, the National Security Agency, and six of CISA’s international partners. That document outlines a number of core principles to guide software manufacturers in building software security into their products from the start. Those principles include having software makers – rather than their customers – “own” the security outcomes of their technology products; embracing radical transparency and accountability; and building organizational structures that foster top-down commitment to software security.
While much of the federal government’s guidance comes in the form of “suggestions” for private sector firms, the Biden Administration’s Cyber Executive Order (#14028) has set in motion a range of initiatives and requirements for vendors who do business with the federal government, including using secure development methods, producing software bills of materials (SBOMs) and using automation to help “maintain trusted source code supply chains.”
However, Executive Orders are not laws and must be continued should the occupant of the Oval Office change, putting the long-term impact of 14028 in question. A more enduring approach can be seen in the medical device space, where the Food and Drug Administration (FDA) won broad new authority, via the recently passed PATCH Act, to ensure the cybersecurity of medical devices that are brought to market. Going forward, medical device submissions for FDA approval will be required to include a software bill of materials and adequate evidence to demonstrate the product can be updated and patched.
Changes are due to the broader software ecosystem, as well. That’s especially true of open source software. Open source is the foundation for almost every modern application, but is largely dependent on the work of an invisible, global army of developers and maintainers – many of them unpaid. The risks inherent in this system are clear, as the plight of Denis Pushkarev, author of the popular open-source library core-js, has made clear. Pushkarev served a sentence in a Russian prison for murder. He is now out of jail and struggling to make ends meet in a country that is a pioneer in software supply chain attacks and whose economy is crippled by steep sanctions after its unprovoked attack on neighboring Ukraine. All the while, millions of software applications across the globe continue to rely on Pushkarev’s library.
Pushkarev’s situation is not unusual. A recent survey of 300 open source maintainers by the firm Tidelift found that, depite increasing demands, most still aren’t being paid for their work. Specifically, 60% of maintainers described themselves as “unpaid hobbyists,” while only 13% describe themselves as professional maintainers earning most or all of their income from maintaining projects.
And, while calls for better open source security grow louder, over 50% of maintainers surveyed by Tidelift were not aware of new security standards initiatives like OSSF scorecards, SLSA, and the NIST SSDF. Of the maintainers aware of one or more of these standards, less than half (43%) have begun work to align to these industry standards or said they plan to begin work within the next year.
The fix? Invest in security. More than 8 of 10 professional open source maintainers (81%) spend more than 20 hours per week maintaining their projects, compared to 27% of semi-professional maintainers, and only 7% of unpaid hobbyist maintainers.


Pingback: Researcher: malicious packages lurked on npm for months – Raymond Tec
Pingback: Is a DEF CON Village the right way to assess AI risk? – Raymond Tec
Pingback: Attacks on APIs demand a Security Re-Think – Raymond Tec