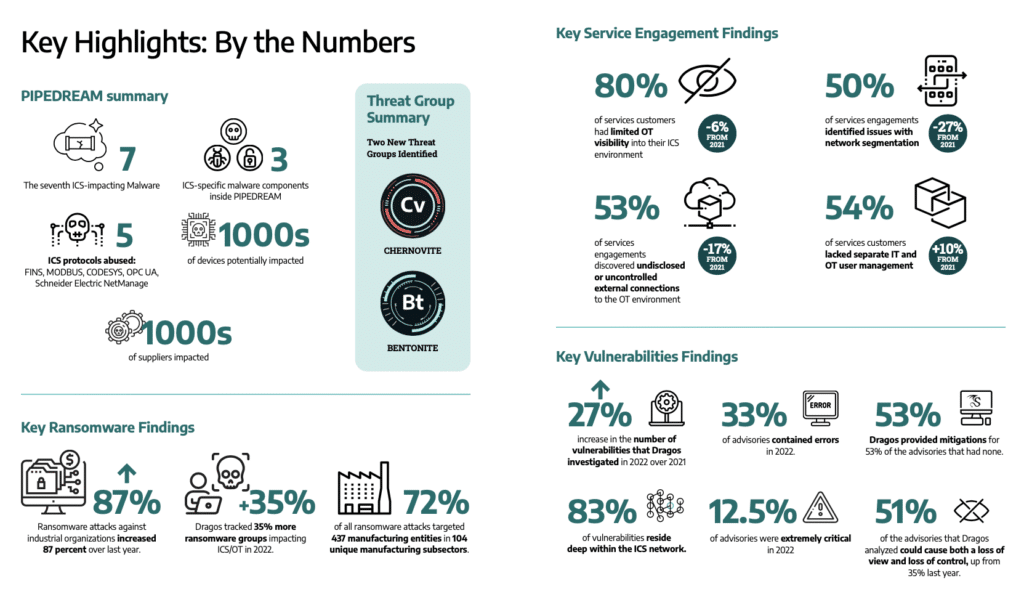
Cyberattacks on industrial control systems (ICS) jumped in 2022, with an 87% jump in ransomware attacks on industrial organizations and a 35% increase in the number of ransomware groups targeting industrial control and operational technology (OT) systems, according to a report by Dragos Security, a cybersecurity firm that specializes in securing ICS systems.
The Dragos ICS/OT Cybersecurity Year in Review for 2022 found cause for concerns, with more cybercriminal and nation-state groups targeting industrial firms in 2022. The last year also saw the emergence of a new ICS focused threat group, Chernovite, and Pipedream, a next-generation ICS hacking platform the group developed that is capable of targeting technologies by multiple vendors systems.

The impacts of Russia’s war on Ukraine was also felt in the industrial cybersecurity space, with Russian cyberattacks on Ukrainian critical infrastructure a feature of the early stages of the conflict, as well as an increase in attacker interest in liquid natural gas facilities that may reflect an effort by the Russian government to frustrate Europe’s shift away from Russia as an oil and gas supplier.
Chernovite Group’s emergence highlights poor visibility
The sudden emergence of Chernovite and Pipedream in 2021 underscores one of the challenges facing the ICS community: a lack of visibility, said Dragos Co-Founder & CEO Robert M. Lee in a briefing on the findings in the new report.
Iranians Indicted in SamSam Ransomware Scheme
“This is a group that we weren’t tracking – nobody was tracking. When they showed up they were already a Stage 2 actor capable of doing destructive and disruptive effects” he said.
Chernovite’s emergence was overlooked because, by Lee’s estimate, only around 5% of global infrastructure is being actively monitored for threats, giving groups like Chernovite plenty of space to hone their attacks and test their wares without attracting notice.
“We have a lot less visibility than people realize, globally,” Lee said. “If all of our efforts are going in to preventing attacks but only 5% of companies are actually looking inside the house, you’re not going to see as much (sp) threats as you’d like.”
Report: Hacker group behind Trisis Malware expanding Activity in Middle East
The group’s ICS-specific malware, Pipedream, joins a short list of malicious software designed explicitly to infect and control industrial control systems. That list includes the legendary Stuxnet malware, designed to attack Iran’s Uranium enrichment facilities, as well as BlackEnergy2, deployed against Ukraine’s electrical grid, Crashoverride, Trisis which targets Schneider Electric’s Triconex platform and Industroyer2.
Pipedream: a weapon of cyberwar
Compared to those, Pipedream is next-level malware, which Dragos is confident was developed by a “state actor” and intended, initially, to target electric and liquid natural gas facilities in the US and Europe, Lee said.
Pipedream marks the first time researchers have uncovered malware that can be disruptive or destructive in industrial control systems across industries, Lee said. Previously, ICS-focused malware was specific to certain platforms used in a certain type of facility. For example, Crashoverride and Industroyer2 only worked in electrical substation facilities. The Trisis malware only worked in chemical facilities that used the Triconex platform. Pipedream doesn’t have those limits, and could be used by attackers to target any number of platforms and facility types.
“You could put it in a data center. You could put it in a wind farm. You could put it in an oil and gas refinery or offshore rig,” Lee said.
In part, that is because of changes in the way that ICS software is being designed and deployed, Lee said. Historically, ICS infrastructure has been very heterogenous, varying depending on the type of facility and the ICS systems used. But digital transformation within industry that has brought with it a shift to homogenous infrastructure with common network protocols, libraries and software stacks. That makes cross-industry threats possible.
Spotlight: as Attacks Mount, how to secure the Industrial Internet
While the initial targets were focused on electric and LNG facilities, Pipedream could have targeted a wide range of facilities.
“This is a state level, wartime capability,” he said “The state actor responsible for this – there’s no chance this wasn’t their go to package to bring down infrastructure.” Fortunately, the malware was discovered before it could be widely deployed and used to carry out attacks. Lee said his company worked with an “undisclosed third party” to find and analyze the Pipedream malware and estimates the group behind it initially targeted a dozen LNG and electrical facilities in the US and Europe. Had the malware actually been successfully deployed on those targets, the world could have seen a substantial disruption of critical infrastructure as a result, Lee said.
While the Chernovite group was frustrated in that effort, the threat remains, Lee said. “Something didn’t happen, but I don’t think people understand how close it was to happening.” The group is still active and working to develop the framework. Dragos expects to see it deployed in the future and there is no easy way to “fix” the Pipedream risk because it leverages native functionality and protocols in existing ICS systems such as FINS, MODBUS, CODESYS, OPC UA, and Schneider Electric NetManage rather than exploitable software flaws. In essence: the malware uses the features of ICS systems to undermine the integrity of industrial facilities.
While liquid natural gas facilities aren’t a new target of interest for cyber adversaries, Lee said that – in the wake of Russia’s invasion of Ukraine – there does appear to be more interest among malicious actors in probing the weaknesses of LNG facilities in the U.S. and Europe. While its unclear what the motivation is, that may reflect an interest by Russia and its allies in disrupting LNG flows to Europe, where countries are rapidly shifting their energy infrastructure away from Russia-supplied oil and gas.
Time to invest in detection
With no patch to deploy to stop Pipedream, ICS operators need to invest more in detection and response as a way to limit the risk of compromise, Lee said. “You have a zero percent chance against this adversary if you just do prevention. You must do detection and response,” he said.
Beyond that, Chernovite is just one of a handful of ICS hacking groups with names like Kamocite, Xenotime and Electrum that spent 2022 conducting reconnaissance, building capacity and engaging in initial access activity targeting across industrial sectors, Dragos said.
Ransomware reaches out to Industry
Ransomware was the other big story of 2022, with an 87% increase in ransomware attacks on industrial systems, Dragos reported. Of the more than 500 ransomware attacks Dragos tracked, 437 (72%) were against manufacturing firms, with smaller numbers of attacks on food and beverage makers, pharmaceutical companies and oil and gas firms.
Attacks by the Lockbit, Conti and BlackBasta groups accounted for most of those.
The focus of those groups on manufacturing is likely a byproduct of their lower levels of cyber maturity and poor visibility into their own environments, Dragos said. In fact, 89% of manufacturing firms had poor visibility into the cybersecurity of their OT (operational technology) environments, Dragos reported. Poor IT security practices also abound in those firms.
“There’s just a ton of shared credentials between IT and OT networks,” Lee said.
Focus on detection and mitigation
The past year leaves many challenges ahead for industrial firms. Chief among them: a shift in thinking and approach from prevention to detection and response. For example, the focus on patching vulnerabilities in ICS systems often pulls resources and attention away from activities that are more effective in stopping or blocking attacks in order to patch low severity flaws or those that are unlikely to play a part in an actual attack, Lee said.
‘We want to be very precise about vulnerabilities,” Lee said. “A lot of them are not useful. A lot of vulnerabilities are not things that can be weaponized by adversaries.”
At the same time, vulnerability provide by ICS manufacturers is often inaccurate and downplays the severity of security issues in ICS software. Dragos counted 2,170 CVEs related to ICS – 20% more than 2021. Half of them (50%) allow attackers to impact control and visibility on affected system, but almost as many (49%) don’t have any impact on control or visibility and present a low risk.
Also, more than a third of the published ICS vulnerability reports (34%) contained inaccurate information about the flaw. That includes incorrect description of the vulnerability or what hardware and software it affected, incorrect mitigation advice, and so on.
CVE severity ratings on ICS vulnerabilities also downplayed the actual cyber risk, Dragos found. Seventy percent of the vulnerabilities Dragos studied should have had a higher severity rating than they did, Lee said.
That leaves infrastructure owners in a tough place: conditioned to invest heavily in prevention, but struggling with a lot of noise and incorrect information to work with.
The solution, Lee said, is for industrial firms to invest heavily in detection, response, and mitigation while also working hard to filter out the signal from the noise about vulnerabilities and threats to ICS systems.


Pingback: The Week in Security: Russian hackers targeted U.S. gas and electric, malicious PyPI packages show prowess - Ciberdefensa
Pingback: HPE’s Cole Humphreys envisions meaningful supply chain security for enterprise IT - SiliconANGLE