Cybercriminals are specializing as they try to extract the maximum value out of email account compromises, researchers at UC Berkeley and Barracuda found.
A new study finds that cybercriminals are specializing in an effort to make more efficient work of compromises and, presumably, to get more bang for their buck.
A new study by cybersecurity firm Barracuda Networks and researchers at the University of California, Berkeley shows that cyber attackers who compromise email accounts often fail to exploit their access, preferring to sell account access and intelligence gained from their compromise to other cyber criminals.
Rise Of The Email Compromise Specialist
Researchers from Barracuda and UC Berkeley studied 159 compromised accounts from 111 organizations, observing how the account takeovers happened; how long attackers had access to the compromised accounts; and how attackers extracted and used information from the compromised accounts.
The findings showed that while most compromises (53%) last for less than a day, a large minority of takeover incidents (37%) last a week or longer. Many times, multiple accounts—and even multiple cybercriminals— are involved.
Gaining access to email accounts creates the opportunity to compromise and gather information in other applications and systems. Mike Flouton, a Senior Vice President of Email Security at Barracuda said that while “smash and grab” phishing attacks that attempt to compromise as many accounts and gather up information still happen, cyber criminals are specializing
Password Psychology: users know reuse is bad, do it anyway
The goal is to gain access to a few accounts at an organization and perform reconnaissance, he said. The information gathered during reconnaissance, including intelligence on email signatures used, conversations going on within the organization and internal systems can enable future attacks or be sold to other cybercriminals.
For example, Barracuda found that for 93 percent of the compromised accounts they observed, attackers didn’t exploit the compromised account for phishing attacks during the time period researchers analyzed. Researchers said that the information gathered by observing the accounts could help attackers set up impersonating domains for future hacks or launch conversation hijacking attacks.
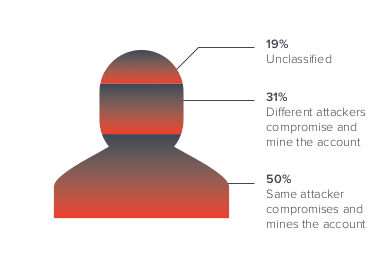
The researchers posit that specialization within the cybercriminal underground and cooperation between different cybercriminals is what cements this division of labor. In fact, in 31% of accounts observed by the researchers were compromised by one attacker and then used by a different attacker who mines for information and extracts value from the account.
Back To Security Fundamentals
Like other security firms, Barracuda said it has seen changes in the content of phishing attacks in the advent of the COVID-19 pandemic and the mass migration to remote work. Still, the fundamentals of phishing campaigns remain the same.
Podcast Episode 135: The Future of Passwords with Google Account Security Chief Guemmy Kim
Poor security hygiene such as password reuse was a popular avenue for actors to gain access to business accounts. Researchers found that 20 percent of compromised accounts were the result of password reuse, meaning the password linked to the compromised account had appeared in at least one online password data breach.
Phishing: Just The Beginning
The lesson is that protecting an organization against phishing attacks is only the beginning; access to accounts is possible through other means, as well.
Report: Cybercriminals target difficult-to-secure ERP systems with new attacks
Barracuda recommends organizations look to suggests that “post-compromise-tools, such as forensics, automated incident response, and post-delivery threat removal” are key to containing email compromises.
The report, Spear Phishing: Top Threats and Trends was released on Thursday. You can find the full report here.


Pingback: As Election Day Nears, Kremlin Leans on Hackers-for-Hire | The Security Ledger
Pingback: As Election Day Nears, Kremlin Leans on Hackers-for-Hire | Check My Ad Blocker