Practical quantum computing isn’t here yet. But a new survey by DigiCert suggests that isn’t stopping IT pros from prepping for a post-quantum reality…even if they aren’t exactly sure what that means.
Depending on which article you’re reading, quantum computing is either nigh or a Big Lie perpetrated on the public by companies interested mostly in touting their own technology chops. But a survey of some 400 organizations by DigiCert suggests that IT professionals are taking the security threat posed by quantum computers seriously…even if they aren’t exactly sure what that threat is, or when it will arrive.
DigiCert’s Post Quantum Crypto Survey for 2019 (download it here) found that IT professionals are acutely aware of the advent of quantum computing and recognize its potential to both accelerate technological progress and shake up established security protections, such as data encryption.
Companies like Google, IBM and Microsoft have poured millions into developing functional quantum computers. In recent years, those firms as well as academic researchers working in the U.S., Europe, China and elsewhere have notched successes. Last week, for example, Google announced that it had achieved “quantum supremacy” using a “programmable, superconducting processor.” Quantum “supremacy” is defined as the ability of a quantum computer to solve a computing problem more quickly than a classical computer. In the case of the Google experiment, the company said it had developed a 53 qubit quantum processor dubbed “Sycamore” that was able to complete a task in a little more than 3 minutes that would take approximately 10,000 years to complete using state of the art classical computers.
[Listen: Podcast Episode 133: Quantum Computing’s Security Challenge and Life After Passwords]
Quantum computing will give a huge boost to security. But Experts have warned that the exponential increase in computing power that quantum computing will bring will render current encryption algorithms toothless. Thw National Institute of Standards and Technology (NIST) has warned of what it calls “a looming threat to information security” posed by quantum computers and asked the public for help in heading off a security disaster by developing post-quantum cryptography that will stymie even next generation computers.
Quantum is (kind of) here
The Google experiment suggests that the quantum future is upon us, but that’s not the whole story. As impressive as the company’s Sycamore processor is, it is still a far cry from being powerful enough to break modern encryption algorithms like RSA-2048 or AES, Tim Hollebeek, an Industry and Standards Technical Strategist at DigiCert told me.

“The kinds of computers Google is talking about are not a danger to cryptography,” Hollebeek said. He estimates that processors that create quantum states on millions of qubits will be needed to break modern cryptography: a big leap from the few dozen qubits Google has demonstrated. What Google’s experiment does show is the rapid pace at which quantum computers have become more powerful than two or three years ago, Hollebeeek said.
Post-quantum crypto: Check…?
DigiCert’s survey highlights some of the confusion that’s permeating IT departments when it comes to crypto. On the one hand, announcements like Google’s and the press they receive have put IT departments on notice that the quantum computing train is coming and that it puts current security technologies at risk. On the other hand, there’s considerable uncertainty about what that means.
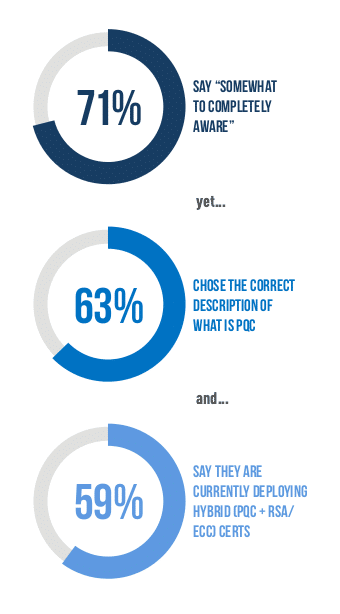
The survey, which polled IT professionals within 400 enterprises in the US, Germany and Japan found that seven in ten described themselves as “somewhat” to “completely” aware of post-quantum cryptography. However, when DigiCert followed up with a question designed to test if their respondents truly understood what post-quantum cryptography means, just 63% defined that correctly.
Even more worrying: more than half (55%) of respondents to DigiCert’s survey said that quantum computing is a “somewhat” to “extremely” large threat today while almost six in ten respondents (59%) told DigiCert that they were already deploying hybrid post quantum and RSA or Elliptic Curve Cryptography certificates in their organization. That last one is a dubious claim, as the availability of post quantum certificates is still limited to early testing situations.
“It is worrying if people think that they are more ready than they are,” Hollebeek told me.
Agility is the key
The truth is that nobody knows when practical, commercial quantum computers will arrive. Hollebeek said it could be a decade or more in the future–or a matter of years. However, once quantum computers become viable for solving what Hollebeek describes as “financially valuable” problems, it stands to reason that their development and use will accelerate.
In the meantime, with quantum computing in its infancy, the important thing is not to be “quantum safe,” so much as it is to be ready for whatever comes, Hollebeek said. “Crypto agility” refers to the ability of organizations to embrace new, stronger encryption as it becomes available and necessary.
The near future is almost certainly hybrid: with both classical and quantum computers at use solving a wide array of problems. The transition from one to the other may take a generation or more. “It’s not an exaggeration to say that it will be a decades long effort to replace all the world’s cryptography,” Hollebeek told me.
In the meantime, companies will need to find ways to make due in the meantime: building crypto agility into the design of new products and developing ways to protect the mountains of legacy hardware and software that are already in the field.



So long as quantum computing results remain probabilistic, not deterministic, and error correction remains elusive, the quantum threat will remain purely theoretical. Without reliably repeatable Qbit precision any Shor’s algorithm or brute force attack will never return a successful result. Furthermore, as the The National Academy of Sciences report points out, by simply bumping encryption from 128 to 256 any quantum threat will be defeated. For more reality on this subject, see the papers and reports on our web site. https://www.trustwrx.com/index.php/papers-reports/