The security firm Cybereason has uncovered a persistent cyber espionage attack on telecommunications companies worldwide to steal data on high-profile users and then spy on them.
The Boston-based firm identified the attack at a large telecommunications provider–which researchers call Operation Soft Cell–last year, according to a report the company published online. The attack was aimed at obtaining data of high-value targets and resulted in complete network takeover, researchers said.
The attack used tools and techniques commonly associated with a known China-based threat actor, APT10, so researchers assume this is the likely culprit behind the attack, they said.
“This attack has widespread implications, not just for individuals, but also for organizations and countries alike,” researchers said. “This is another form of cyber warfare being used to establish a foothold and gather information undercover until they are ready to strike.”
The attacker in question had been active about two years–engaged in activity typically conducted by state-sponsored actors–when researchers discovered the activity last year, according to Cybereason.
Criminals, Not State Actors, Target Russian Oil Company in 3-Year Cyber Attack
“The threat actor mainly sought to obtain CDR data (call logs, cell tower locations, etc.) belonging to specific individuals from various countries,” according to the report. “This type of targeted cyber espionage is usually the work of nation state threat actors.”
CDR, or call detail record data, are basically detailed metadata logs generated by a telecom provider that connects calls and messages between those on both ends of the call. While these logs don’t contain actual call or message content, they do provide significant insight into a person’s life, such as who is talking to who, where people are located, and what device is being used.
The attacker basically tried to steal all data stored in the telecom company’s active directory, compromising every single username and password in the organization along with other personally identifiable information, billing data, call detail records, credentials, email servers, geo-location of users, and more, according to Cybereason.
Criminals, Not State Actors, Target Russian Oil Company in 3-Year Cyber Attack
Two-phase attack
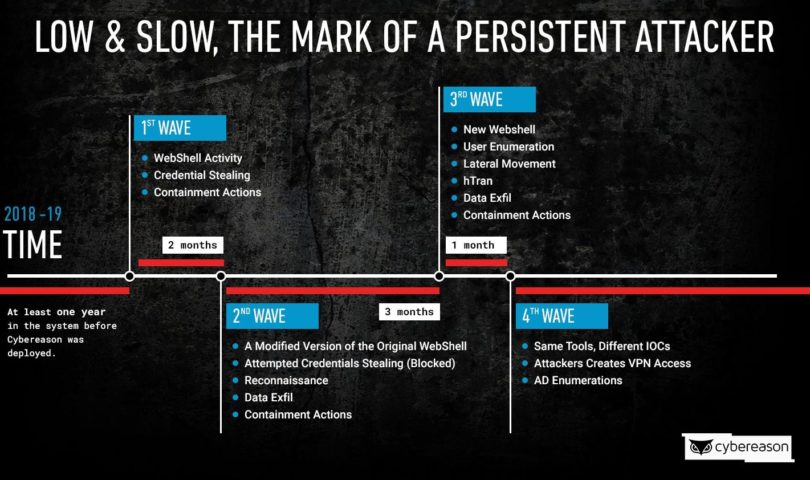
Researchers describe the attack in two phases, beginning with a web shell–identified as a modified version of what’s called a China Chopper shell–running on a vulnerable, publicly-facing IIS server. From the attackers gathered information about the network and propagated across it, attempting to compromise critical assets, such as database servers, billing servers, and the active directory, researchers said.
Eventually, the telecom provider noticed the malicious activity and began steps to remediate the attack, at which point the attacker gave up. But it was only a pause in the action, researchers said, as several months later the threat actors returned with similar infiltration attempts, along with a modified version of the web shell and reconnaissance activities.

This continued for a four-month period as attackers continued to attack while the telecom would defend itself, with the threat attack ceasing and resuming the attack two more times during that time frame.
‘Low-hanging fruit’
Telecommunications companies are easy and popular targets for cybercriminals, for a number of reasons. They don’t have stores of payment information, like financial institutions, nor do they have intellectual property, like technology companies. However, CDRs in and of themselves are valuable data stores, particularly for spying and surveillance campaigns.
“Given the volume of valuable data of their clients, telcos are an attractive low-hanging fruit for cybercriminals,” said Ilia Kolochenko, founder and CEO of web security company ImmuniWeb.
Moreover, as part of a worldwide network of critical infrastructure, disrupting or disabling telecommunications networks can cause panic and havoc very quickly among the general population, another reason to attempt to take down telcos, according to Cybereason.
Unsecured Database Exposes Data of 80M U.S. Households
“Any entity that possesses the power to take over the networks of telecommunications providers can potentially leverage its unlawful access and control of the network to shut down or disrupt an entire cellular network as part of a larger cyber warfare operation,” researchers wrote in the report.
Lackluster security practices
Kolochenko said he’s not surprised by the attack because telecommunications companies also are often woefully behind on implementing the latest security practices, making them even more vulnerable to large-scale attacks.
“In my experience, many large telcos today struggle to maintain a decent level of cybersecurity due to tough competition and limited budgets, let alone a continuous increase of new hardware and infrastructure mushrooming in their premises to stay up-to-date with the industry progress,” Kolochenko said. “Consequently, some don’t even have any form of up-to-date asset inventory, privilege segregation or internal security monitoring.”
Cybereason made several recommendations to advise telcos how to beef up security to avoid persistent attacks like the one it laid out in its report. Researchers recommend adding an additional security layer for web servers, and exposing as few systems or ports to the Internet as possible. For the web servers and web services that are exposed, they advise telcos to ensure that they are all patched.
Other recommendations include using an EDR tool to give visibility and immediate response capabilities when high severity incidents are detected, and proactively hunting the network environment for potentially malicious assets periodically, researchers said.

Pingback: Ahead of Black Hat: Fear and Pessimism in Las Vegas | Raymond Tec
Pingback: Episode 154: Richard Clarke on Defending the Fifth Domain | Raymond Tec