Iranian state-sponsored hackers are regrouping after the shutdown last year of their main security forum, migrating to other forums and making new connections for potential cyber-response against mounting political pressures from the United States and Europe, according to a new report.
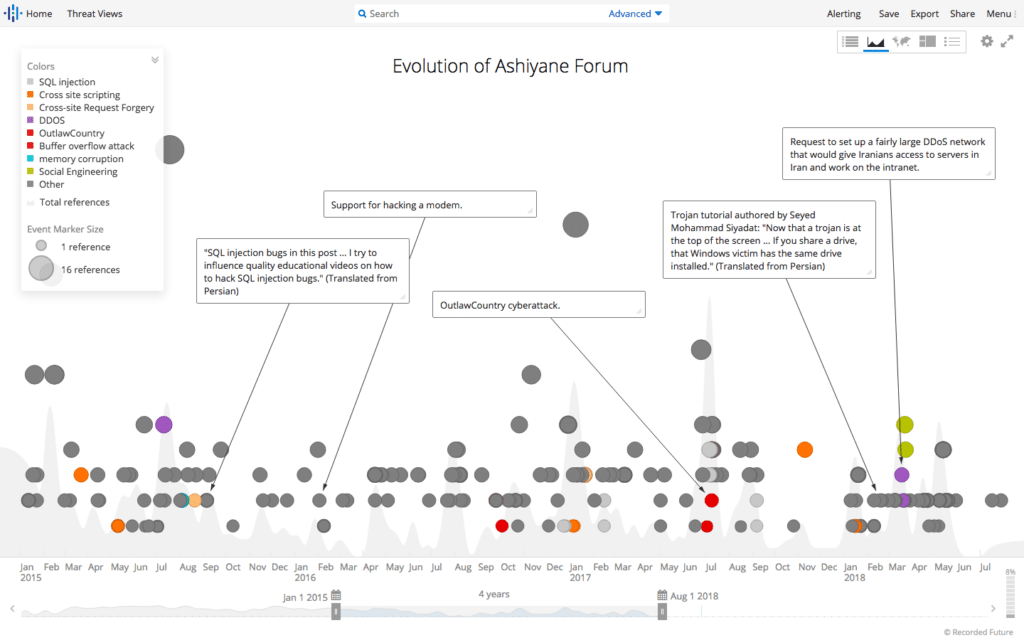
Recent observations from Recorded Future find that Iran’s hacker community is in a state of flux after the closure of Ashiyane Forum, the first and largest security forum in Iran, in August 2018. The firm believes the forum–and its founder, the Ashiyane Digital Security Team–was a hub of information and activity for Iranian advanced persistent threat (APT) actors, who even discussed future attacks there.
So-called “gray hat” security company Ashiyane Digital Security Team–which has strong ties to Iran’s Islamic Revolutionary Guard Corps (IRGC)–set up the forum in 2002 ostensibly as a way to educate Iranian users and network administrators on security by finding vulnerabilities within computer networks. Group members would use these vulnerabilities to deface websites–such as those of Thai and Indian government organizations–to make their point.
However, Ashiyane Digital Security Team and its founder Behrooz Kamalian got into some hot water last year for running gambling websites–an illegal and serious offense in Iran–resulting in prison time for Kamalian. He recently was released and is currently attempting to build new businesses, Recorded Future found.
Listen to this podcast: Episode 104: Mueller’s Cyber Eye on the Russian Guys also Reaper Drone Docs Stolen
Iran’s APT network
Recorded Future has been tracking the activity of Iran’s advanced persistent threat (APT) actors for some time, monitoring the ecosystem of private security contractors, the Iranian government and how they intersect to launch cyber attacks.
In a previous report published last May by Recorded Future’s Insikt Group, researchers shined unprecedented light on the structure of Iranian contractors working for the Islamic Republic to accomplish offensive cyber campaigns. That report documented the relationship between the Iranian government, contractors used for offensive cyber operations, and the trust communities that begin with Iranian security forums like Ashiyane.
Indeed, the founder of the forum, Ashiyane Digital Security Team, is the known actor behind many of Iran’s state-sponsored cyber campaigns, including hundreds of attacks against U.S. and Israeli government organizations.
See also: Report: Obvious Security Flaws Make ICS Networks Easy Targets
The company also has been responsible for politically-motivated retaliatory attacks, according to Recorded Future. For example, when Sunni Arab hackers brought down a major server hosting most Shia religious websites in Iran, Ashiyane Forum responded by bringing down 300 Arabic websites by attacking five of the major servers belonging to the hackers.
In that attack, the Department of Justice and other industry members identified that members of Ashiyane Digital Security Team were operating on behalf of the IRGC.
Moving targets
Now with the forum out of commission for the foreseeable future, hackers are likely “searching for new communities that provide the same topical discussions and interactions, or rely increasingly on other already established — albeit less popular — forums,” researchers said in the report, released Wednesday.
Recorded Future reviewed posts from over 20,000 Ashiyane Forum members from 2014 to 2018. Of the 18,060 users active before Ashiyane Forum shut down, only 4 percent of users had monikers with exact matches on other Persian, Arabic, Russian or English forums, researchers said.
Of these exact matches, two in particular seem likely candidates for where Iran’s APT actors will continue the activity where they left off on Ashiayne Forum: VBIran.ir and Persian Tools forum, according to the report.
“The migration is important because information security teams should be tracking threat actors’ tools, tactics and procedures, and using the ongoing intelligence to identify their respective organization’s technical security control gaps,” said Levi Gundert, vice president of intelligence and risk for Recorded Future. “Following forum activity helps security practitioners understand TTPs that may be used in future attacks.”
Mounting political pressures
While Recorded Future has no specific insight into these future attacks, they are inevitably on the horizon, researchers believe. Since at least 2009, Iran has regularly responded to both regional provocations and international sanctions by conducting offensive cyber operations, the firm said.
“Primary targets of such attacks have been Saudi Arabia, Israel and Western organizations, as well as Asian petrochemical and aviation companies,” according to the report. “The sophistication of these attacks has ranged from social media hijacking and website defacement to highly destructive campaigns, like the attack on Saudi Aramco and sophisticated espionage campaigns against Western, Middle Eastern and Asian targets.”
In the United States, Iranian hackers have previously targeted several specific industries–banks and financial services, government, critical infrastructure and oil and energy–using a network of contractors and universities to conduct state-sponsored cyber operations.
Iran is currently struggling under the weight of sanctions by the United States, which are taking their toll, according to published reports. Recent news also surfaced that last year President Trump’s national security adviser John Bolton directed the National Security Council to provide the White House with military options to strike Iran, attacks that would surely fuel the fire.
To make matters worse, Europe also recently sanctioned Iran, adding two Iranian individuals and an Iranian intelligence unit to the EU’s terrorist list. Iran has promised retaliation for these sanctions.
If history serves, some of these retaliations could be cyber-based, researchers said. “We continue to observe offensive activity out of Iran,” Gundert acknowledged. However, it’s difficult to say in what form and from where the next attack will come, as “the Farsi speaking forums don’t traditionally telegraph future attacks,” he said.


Pingback: DoJ Charges Huawei Execs in Broad Indictment Spanning 10 Years of Criminal Activity | The Security Ledger