A small group of cybercriminals are responsible for the most damaging cyberattacks–often with the help of state sponsorship. Still, low-level criminal activity on the dark web still poses the most widespread and immediate security threat, with cryptocurrency mining, ransomware and malware all on the rise, a recent report has found.
While much of the attention of security researchers focuses on bad actors operating on the dark web, it’s really a underworld of sophisticated cybercriminals who are responsible for the cybercrime resulting in the biggest financial losses, according to the 2018 State of Cybercrime Report from Secureworks.
“The distinction is important because while commodity malware can be highly damaging it is frequently highly automated and not customized for the victim,” Secureworks CTU Researcher Keith Jarvis told Security Ledger. “The sophisticated attacker has the time and resources to interact with the victim’s network. They can learn the organization’s business and financial operations, identify where important data is stored, and even monitor how internal security teams respond to incidents.”
Report: Cybercriminals target difficult-to-secure ERP systems with new attacks
While these actors may sell goods and services on the dark web, it would be difficult for security experts and researchers to find them or their crimes by monitoring activity there, researchers found. Instead, the worst and most sophisticated cybercriminals developing and selling the ransomware and malware deployed by nation-states operate “deep in the trenches,” according to the report.
“They are the sophisticated threat groups who steal millions of dollars in one day by penetrating banking networks and disabling anti-fraud controls in order to perform near-simultaneous cash withdrawals from ATMs all over the world,” researchers wrote. “They are the well-organized gangs defrauding buyers to the tune of hundreds of thousands or even millions of dollars by inserting themselves into the middle of large business transactions or real estate purchases.”
That’s not to say that every-day cybercriminals aren’t dangerous as well. Low level cybercriminals are steadily engaged in activities that serve as “background noise,” working under the radar and impacting businesses across the globe, researchers found.
Dark Web Bolsters Cybercrime
Researchers used a combination of dark-web monitoring, client-brand surveillance and automated technical tracking of cybercriminal toolsets to come up with the results of the study, which were gathered between July 2017 and June 2018 across 4,400 companies.
Even if they are not as high-impact as more sophisticated attacks, more common methods of cybercrime such as ransomware, banking malware and point-of-sale memory scrapers continue to pose a major threat with their availability for purchase on the dark web, researchers said.
Cybercriminals are getting more creative and adaptable as well. With the rise in the use and investment in cryptocurrencies like Bitcoin and Monero has come a rise in a new form of cybercrime: cryptocurrency mining, which Kaspersky Labs has deemed the new ransomware. Researchers found that even though both leading cryptocurrencies have lost half their value since January, illegal mining of cryptocurrency provides a lucrative return on investment and–despite reports to the contrary–is not slacking off.
This type of crime also seen in the criminal community as “less morally objectionable and less likely to draw law enforcement intervention than other types of attacks,” another reason for its continued popularity among low-level cyber criminals, researchers said.
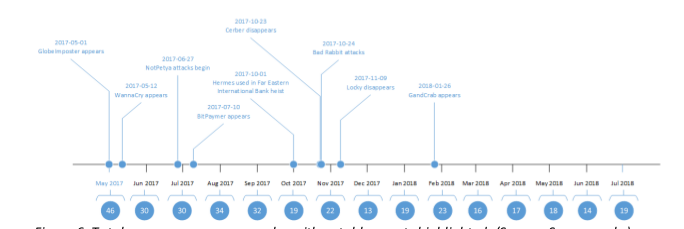
The report investigated trends on the dark web to see how they are affecting which cybercriminal methods remain most prevalent. Researchers found that spam e-mail remains the main way malware is delivered to users. However, actors delivering malware this way are forgoing the rent of million-bot-strong spam botnets like Cutwail, Necurs and Phorpiex in favor of developing customer malware.
Commodities that do remain valuable to bad actors are data sets and access to systems–such as user passwords–both of which are still for sale in large volumes on the dark web, researchers found.
In fact, personally identifiable information (PII)–including full biographic dossiers, payment card data and other bulk data sets–are regularly offered for sale in underground forums. Such value placed on data means clear financial gain for bad actors, guaranteeing that they are going to continue to try to infiltrate systems and steal sensitive information, which keeps consumers and businesses risk, researchers said.
Different Actors, same Business Peril
While the report paints a picture of two different groups of cybercriminals threatening the security of business data and systems, they both can cause what Jarvis said is the biggest threat for organizations today–business continuity, or a loss thereof.
“There is a short and intermediate-term threat from ransomware, worms or other destructive attacks that impact an organizations operations,” he said. “It can take weeks to recover from such attacks and if any data is permanently lost, some aspects of the business may be irrecoverable. In cases where intellectual property theft occurs, for example by government-operated attackers tasked with industrial espionage, the effects of technology transfers to competitors may not be felt for years.”
Researchers agree that organizations should step up security efforts to combat attacks by both types of cybercriminal, albeit with different approaches.
For the more sophisticated hacker, security researchers need, obviously, more sophisticated security methods in place. Jarvis recommends a combination of capabilities to track activity and get ahead of cybercriminals. Like some of the methods Secureworks employed in their report research, they can include a dark-web monitoring and client-brand surveillance with automated technical tracking of cybercriminal toolsets to provide a holistic view of the threat these actors pose, he said.
“Security teams need threat intelligence that helps them understand not just threat actor tools and associated indicators, but also their tactics, techniques and procedures,” to build defenses that can anticipate evolving threats and protect organizations, Jarvis said.
More common and commodity-based cybercriminals have a different psychology altogether than the more sophisticated attackers–they want to make as much money as possible with the least possible effort and risk.
To combat their efforts to disrupt business and steal funds or data, organizations should focus on deterrence in the form of basic security practices that make them harder targets for cybercriminals, Jarvis said. They can do this by implementing best practice hygiene like patching, multi-factor authentication on Internet-facing applications, applying principles of least privilege for users, and implementing layered detective controls, he said.


Pingback: Spotlight: Operationalizing Deep Web and Dark Web Intelligence | The Security Ledger
Pingback: Criminals, Not State Actors, Target Russian Oil Company in 3-Year Cyber Attack | The Security Ledger