Two security firms warn of a flurry of “sextortion” campaigns recently that use new, creative and sometimes extreme methods that leverage personal information, sex-related activity and even death threats to spur victims to pay thousands in ransom fees to hackers.
New analysis of several recent campaigns by Cisco Talos Intelligence Group and by the security firm Barracuda warn of an expansion of these types of attacks. The attacks include using previously leaked user passwords and claims of having videos of victims’ watching porn or proof of victims’ partners cheating on them to extort money from them, according to a blog post by Jaeson Schultz, technical leader at Cisco Talos.

Spammers began bombarding users with a resurgence in sextortion-type attacks in July with predictable attack patterns that make them easily identifiable, according to researchers. Generally, the perpetrator would use e-mail addresses harvested from data that’s been publicly made available through a breach, and then tap one of a variety of methods showing a legitimate reason for trying to wrangle money from victims.
“Based on the success the attackers experienced with previous sextortion campaigns, they have expanded and continued their efforts,” Schultz told Security Ledger.
‘Aaron Smith’ sextortion attacks
To draw their latest conclusions, Cisco Talos researchers extracted and analyzed messages received by SpamCop through Oct. 25, 2018, related to two very similar sextortion spam campaigns, one that began on Aug. 30 and the second that began on Oct. 5, and both of which are still active.
In all they intercepted and analyzed about 58 days worth of spam, including 202,367 emails related to a sextortion campaign with a “From:” header containing the name “Aaron Smith” transmitted from 121,863 unique IP addresses. While the IP addresses are distributed geographically, more than 50 percent of them originated in one of five countries: Vietnam (16.5%), Russia (15.4%), India (8.8%), Indonesia (5.2%), Kazakhstan (4.6%).
“The campaigns analyzed by Talos are examples of large-volume campaigns that utilize publicly available breach data (LinkedIn, Myspace, etc.) as a means of convincing victims the sextortion messages are legitimate,” Schultz explained. “Because the attackers are reusing sending IP infrastructure and BTC (Bitcoin) wallets across different types of extortion scams, we can link these various spam campaigns to the same group of miscreants.”
Though attackers sent more than 233,000 e-mail messages as part of their campaigns, researchers found that the number of unique recipients was 15,826, which is actually fairly low. This is unfortunate news for potential victims, who received an average of about 15 sextortion spam messages. One lucky victim even received a flood of 354 such messages in his or her inbox, researchers said.
Identifiable attack patterns
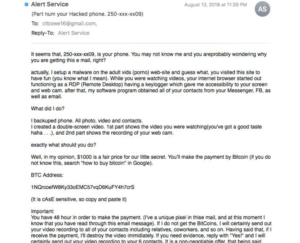
The Cisco researchers were able to identify a reliable pattern to the attacks that pointed to their originating from the same group of attackers. For example, each message included a payment demand between $1,000 to $7,000 across the entire set of sextortion e-mails researchers intercepted. This suggests that the numbers were randomly generated and attackers made no effort to tailor their payment demands to the individual victims, Schultz wrote in his post.
Each sextortion message also contained a Bitcoin wallet address to receive the payment from the victim, with a total of 58,611 unique BTC wallet addresses associated with these two spam campaigns. Judging from the amount in the 83 wallets that had positive balances, attackers have been fairly successful, Schultz noted.
The Bitcoin balances have a current value of about $146,380.31, which is “not bad considering the attackers have only been mailing this particular scam for roughly 60 days, and do not actually possess any compromising material concerning the victim,” he wrote. However, under further scrutiny researchers realized that it’s highly likely attackers are using some of those Bitcoin wallets for other spam-based ransomware campaigns as well.
All told, it seems that “the number of payments made by victims of this particular sextortion attack was quite low,” Schultz told Security Ledger, with a less than .05 percent success rate versus number of sextortion attempts. This low success rate is not for lack of trying, as the recent campaigns show some new tactics and unprecedented creativity in the arguments used to convince victims to pony up the Bitcoin.
Barracuda researchers analyzed a similar (identical?) sextortion campaign, which began in July and is still ongoing. Barracuda found around 24,000 emails since September that were submitted by customers linked to the campaign. The uptake there was similarly paltry: of roughly 1,000 Bitcoin wallets belonging to the attacker, only four transfers were made. Still, with blackmail amounts at anywhere from $1,000 to $7,000, even a low uptake can make them profitable, Barracuda wrote.
The “Aaron Smith” e-mails reveal a hacked passwords to the recipient with a claim that the attacker used the password to gain access his or her computer and created a video of the recipient watching porn, along with a threat to send that video to the victim’s e-mail contacts if they don’t pay. Another variation on this same attack uses a person’s phone number to make the a similar claim and threat to try to extort money.
Other sextortion campaigns related to the same group of attacks get a bit more personal. One e-mail claims that the sender has photographic proof of the victim engaged in sex with a person other than his or her partner, and demands money in return for not revealing the transgression. Another turns the tables on this idea, telling the victim that the sender has proof that his or her partner was the one doing the cheating and asking for money in return for evidence.
One campaign that Cisco Talos researchers believe–with some uncertainty–is from the same attacker crew is downright sinister, Schultz wrote. In these e-mails, an attacker claims to have been paid to kill the recipient of the e-mail but express a change of heart and are now willing to sell information about who is behind the plan to their potential victim.
All bark and no bite?
Even despite attackers’ best efforts, the latest flurry of sextortion attacks so far, while lucrative, haven’t lived up to their full payout potential, and victims aren’t subject to much harm unless they “are frightened into paying the attackers’ demands,” Schultz said.
“This is in contrast to attacks such as ransomware, where the ransom payment literally goes towards facilitating the unlocking of data files encrypted by the attacker,” he said.
However, there still are risks associated with attacks–especially those using hacked passwords and phone numbers–even if those receiving sextortion e-mails don’t take the bait, Schultz warned. Though security professionals discourage it, many people use the same password across many different websites, a practice that can be exploited by a third party who gains access to a sextortion message.
“By sending sextortion messages containing the victim’s e-mail address and compromised password in plain text, it is possible that third parties unrelated to the original sextortion attack–for example if the email bounces to an unintended recipient–could save this email/password combo and use it to attempt to compromise other online accounts belonging to that same victim,” he said.
Moreover, these passwords and other personal information like a mobile phone number could be used to facilitate future targeted attacks against a person if they fall into the wrong hands, Schultz added.

