New malware that uses a device’s own computing power to mine Monero can render an Android smartphone unusable, security firm Trend Micro warned Wendesday.
Called HiddenMiner, so far the malware has been found only in India and China, though researchers expect it will spread.
The malware lives up to its name. Not only does the malware hide in the background out of sight from the user, but it also hides in plain sight—posing as a legitimate Google Play update app in third-party app marketplaces, according to a blog post by Trend Micro mobile threats analyst Lorin Wu.
[You might also like: Consumer Reports: Flaws Make Samsung, Roku TVs Vulnerable]
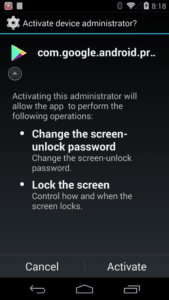
The malware pops up as com.google.android.provider complete with Google Play’s icon, requiring users to activate it as a device administrator. It’s stubborn about it, too—persistently popping up until someone clicks the Activate button, Wu wrote.

Once activated, HiddenMiner starts mining Monero in the background and won’t stop until it drains a battery and ultimately bricks a device, Wu wrote.
“There is no switch, controller or optimizer in HiddenMiner’s code, which means it will continuously mine Monero until the device’s resources are exhausted,” she wrote. “Given HiddenMiner’s nature, it could cause the affected device to overheat and potentially fail.”
Wu compared the malware to a previously found Monero-mining Android malware, Loapi. That malware also drained battery power—so fast it would actually cause the battery to bloat and even begin to melt. Wu noted that Loapi’s technique of locking the screen after revoking device administration permissions also is similar to the technique HiddenMiner uses.
Locked out
There are two key features of HiddenMiner that make it act so maliciously. One is that it locks users out of their own devices by leveraging its role as administrator, which it must do to even run on a device.
Once HiddenMiner is installed, users can’t uninstall it until they remove device administrator privileges, Wu wrote. They can’t do this in the case of HiddenMiner, however, as the malware exploits a bug found in Android OSes—except Nougat, or Anroid 7.0–that locks the device’s screen when a user wants to deactivate its device administrator privileges, she said.
Another key feature of HiddenMiner that makes it so sneaky is that it has a number of techniques to hide itself in devices. One is that it tricks unsuspecting users by emptying the app label and using a transparent icon after installation, Wu said.
It also leverages its role as device administrator to hide the app from the app launcher by calling setComponentEnableSetting(), and remains running with device-adminstrator permission until the user reboots the device again, Wu wrote. These techniques take a page out of the DoubleHidden Android adware playbook, which acts similary, she said.
Emulation can’t catch HiddenMiner, either. The malware checks if it’s running on an emulator by abusing an Android emulator detector found on Github, thereby bypassing detection and automated analysis, Wu wrote.
Mining for cryptocurrency
Trend Micro researchers found Monero mining pools and wallets connected to the malware, with one of its operators withdrawing the equivalent of US$5,360 in one of the wallets. Wu noted that this is “a rather active campaign” in terms of ones already discovered that use infected devices to mine cryptocurrency.
Malware that targets and mines cryptocurrency is on the rise as these types of currencies also become more widespread in use. While Bitcoin and Monero remain the two most popular types of cryptocurrency—and thus the biggest targets of malware campaigns–as of December 2017 there were nearly 1,500 cryptocurrencies in use globally.
“HiddenMiner is yet another example of how cybercriminals are riding the cryptocurrency mining wave,” Wu wrote. For this reason, she said it’s important that users and businesses only download apps from official app marketplaces, regularly update the device’s OS, and practice prudence with the permissions granted to applications.
Wu also suggested, natch, that several Trend Micro security solutions—such as Mobile Security for Android and Mobile App Reputation Service–be used to protect Android users from malware, zero-day and known exploits, privacy leaks, and application vulnerability.
