Hackers believed to be affiliated with a nation-state hacked into emergency shutdown systems at a facility in the Middle East. The attack seemed intended to “cause a high-impact attack with physical consequences,” according to reports from a number of cyber security firms.
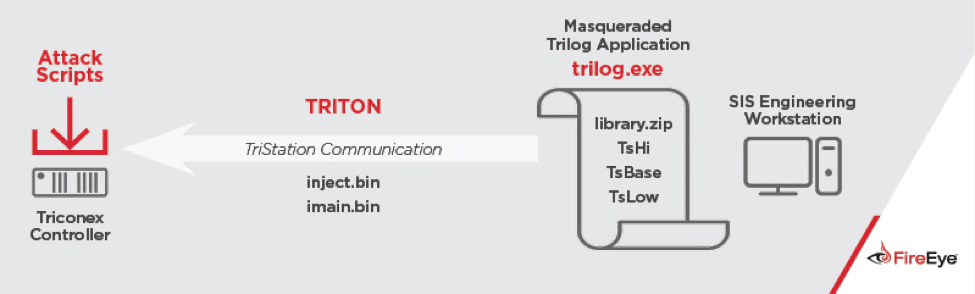
In blog posts on Thursday, FireEye and Dragos Security both reported on the malware platform, variously called TRITON (FireEye) and TRISIS (Dragos), describing it as a new family of malicious software designed specifically to target critical infrastructure systems – in particular Triconex Safety Instrument System (SIS) controllers, manufactured by the firm Schneider Electric.
FireEye described TRITON as an “attack framework” designed to interact with Triconex SIS controllers. It is one of only a handful of malware frameworks purpose-built to target industrial control system (ICS) platforms. The first and most famous of such frameworks is the Stuxnet worm, which was famously used to hobble Iranian Uranium enrichment activities at the country’s Natanz facility in 2009 and 2010.

In a blog post Thursday, FireEye researchers said that the attacker in question first gained remote access to an SIS engineering workstation. The TRITON malware was deployed and used to reprogram the SIS controllers. The malware is capable of communicating using TriStation, a proprietary protocol used by SIS controllers that is not publicly documented, FireEye said.
During the incident, some SIS controllers being reprogram “entered a failed safe state.” That shut down the industrial process and got the attention of the asset owner, who launched an investigation.
The failure was due to a security feature on the SIS controllers, which detected that application code used on redundant processing units failed a validation check and initiated a safe shutdown of the SIS.
FireEye declined to name the customer in question. However, Dragos Security said that the TRITON (or TRISIS) malware had been discovered in “at least one” victim in the Middle East, though there wasn’t evidence it had been used elsewhere in the world.
SIS controllers are safety systems that monitor other equipment and ensure they operate with safe limits. Modifying a SIS wouldn’t cause damage to a facility directly. However, it could prevent key machinery and equipment from functioning correctly. That could make it more likely that a failure would cause physical destruction, FireEye and Dragos noted.
The most likely outcome of an attack on SIS is a plant shutdown, Dragos CEO Robert Lee wrote in a report on the incident. That would result from safety “fail safes” being tripped in SIS devices, which will result in the affected process being halted. Another possible outcome is simply a slowdown in operations of the plant resulting from uncertainty in plant operators, who would then curtail plant activity as they investigate the incident. A third possibility is that SIS is programmed to allow unsafe operation of industrial control systems. Such an attack would have to be accompanied by a simultaneous attack on distributed control systems to cause them to operate in an unsafe way.
FireEye said it had confidence that the TRITON attack was sponsored by a nation-state. “The targeting of critical infrastructure as well as the attacker’s persistence, lack of any clear monetary goal and the technical resources necessary to create the attack framework suggest a well-resourced nation-state actor,” the company wrote.
Among other things, there was no clear monetary objective to the attack, ruling out cyber criminal groups. Further, the attacker deployed TRITON shortly after gaining access to the SIS system on the target network, FireEye noted. That indicates that they had “pre-built and tested the tool which would require access to hardware and software that is not widely available.”
Most malicious software used against industrial and critical infrastructure firms targets traditional IT systems like Windows, Unix or Linux servers or desktop computers or administrative consoles. Software specifically designed to work with industrial control system platforms is far more rare.
However, it is not unheard of. In June, 2016, FireEye warned that newly discovered malware, dubbed “IRONGATE” could enable sophisticated “man in the middle” attacks on applications used with programmable logic controller (PLCs) made by Siemens – the same equipment targeted by the Stuxnet worm.
Industrial control system hardware, software and protocols are widely seen as less secure than traditional IT systems. In August, the firm Synopsys released the results of a study of automated security testing on common communications used in large organizations, including industrial control system protocols. The test found industrial control system security protocols were the least mature of those tested by customers in 2016. “This vertical favors its own niche protocols, which may not have been well-tested over the years,” Synopsys said in its report. On average, the protocols tested by Synopsys failed after 1.4 hours of “fuzzing.” But four of the five least mature protocols were specific to the ICS sector. The “time to first failure” for those protocols ranged from a few seconds to a few minutes.


Look they are real I have confirmed it, contact Alphafasttunnel247ATcyberservices.com for your hack issues ranging from , University Grades change, Email and phone hack for text, whatsapp , call logs,Gps tracking and lots more. He provides proof and trust me he’s real. Ive been ripped severaly they are very good and reliable.
Pingback: Podcast Episode 87: Vulnerability Reports Down the Memory Hole in China and the Groups Hacking ICS | The Security Ledger