In-brief: The hacking group known as APT 3 appears to be a commercial outfit working on behalf of the Chinese Ministry of State Security (MSS), the firm Recorded Future reported on Wednesday.
The hacking group known as APT 3 appears to be a commercial outfit working on behalf of the Chinese Ministry of State Security (MSS), the firm Recorded Future reported on Wednesday.
The company said it can attribute APT3 to a company, Guangzhou Boyu Information Technology Company (aka “Boyusec”), based in Guangzhou, China with a “high degree of confidence” based on open source research and analysis.
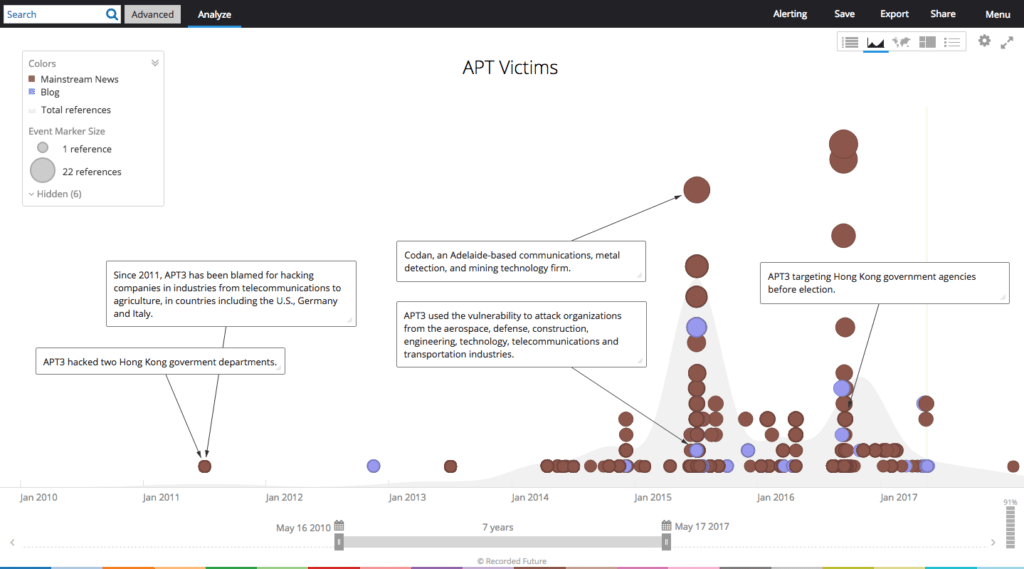
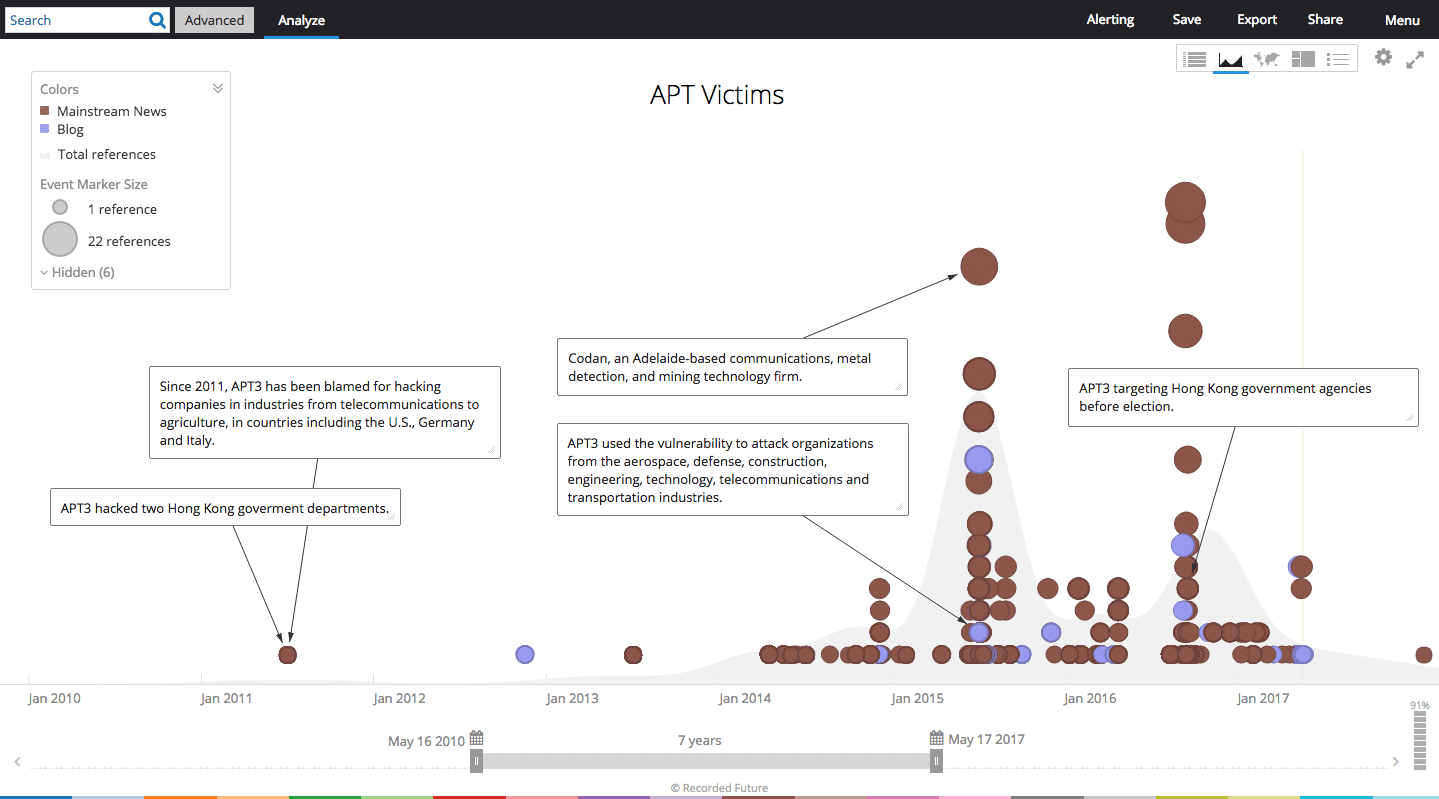
The Recorded Future analysis follows on the heels of an analysis posted on the blog intrustiontruth that connected the activities of APT3 with Boyusec. APT3 has been documented since 2010 targeting a range of companies in the U.S. and UK including defense, telecommunications and technology sectors.
Recorded Future said it used open source research and analysis to corroborate that Boyusec did business mainly with two entities: Chinese networking giant Huawei and a “cooperative partner” known as Guangdong ITSEC. While little was known about the latter firm, Recorded Future verified that it is a subordinate to an MSS-run organization called China Information Technology Evaluation Center (CNITSEC). CNITSEC conducts vulnerability research and may be a provider of information on exploitable software holes to the Chinese military or government, Recorded Future. Boyusec has been working with Guangdong ITSEC on a joint active defense lab since 2014, in addition to working on a joint project with Huawei, Recorded Future said.
The pattern fits with the Chinese government’s preference for using a range of seemingly innocuous, private sector companies to carry out sensitive government and cyber espionage work. Recorded Future said organizations should re-examine any intrusion activity known or suspected to be APT3 and all activity from associated malware families as well as re-evaluate security controls and policies.