In-brief: analysis of the latest leak of sophisticated hacking tools by The Shadow Brokers suggests that the theft was an inside job, the security firm Flashpoint contends.
Did the ShadowBrokers have a broker? That’s one theory about the now-notorious group of cyber criminals who have been hocking sophisticated cyber weapons allegedly lifted from the U.S. National Security Agency to the highest bidder.
Researchers at the cyber security firm Flashpoint on Monday said that analysis of a recent trove of data released by the hacking crew suggests that the advanced exploitation tools now for sale were taken directly from an internal network, not by way of remote exploitation of the NSA, or a lapse by NSA network operators.
Flashpoint said it has “medium confidence” that the tools being offered by ShadowBrokers were first leaked by an insider, but is “uncertain of how these documents were exfiltrated.” The files appear to have been lifted from an “internal system or code repository,” the company said.
[Read more Security Ledger coverage of The Shadow Brokers.]
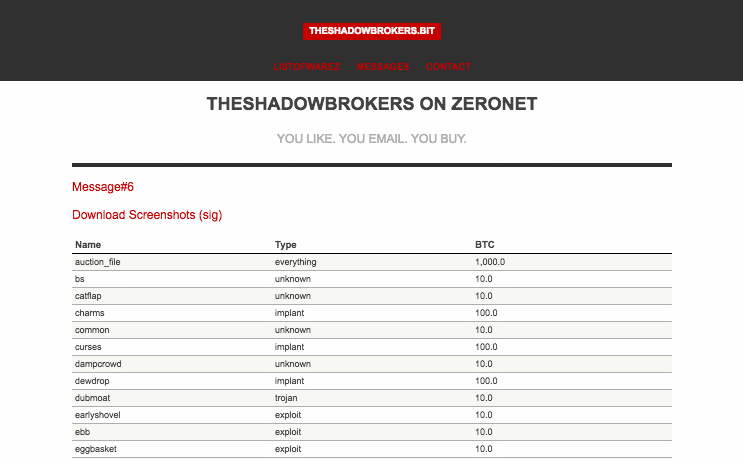
The ShadowBrokers first came to attention in August when the group began offering more than a dozen sophisticated hacking tools for sale in underground marketplaces. Among the tools were software for extracting decryption keys from products like Cisco’s PIX firewalls. That could allow an attacker to spy on encrypted communications sent via Virtual Private Network (VPN) software and other applications. The leaked software have been characterized as “post exploitation” tools that were deployed after a network had been compromised and were likely used by NSA offense cyber teams such as the so-called “Equation Group.”
On Wednesday, a post on the blogging site Medium.com noted the existence of another supposed sale of hacking tools by The Shadow Brokers on ZeroNet, a decentralized, encrypted peer-to-peer network.
In a blog post, Flashpoint’s analysts noted clues in the leaked information to estimate when the data was stolen, which the company says was around 2013. The three-year lapse between that theft and the tools being offered for sale suggests that monetary gain wasn’t the motive for the theft – as the tools would have their most value at the time they were stolen and before vendors had a chance to update and patch security holes the tools exploit.
Also, Flashpoint notes the use of so-called “markdown” language that is used in source code repositories. The presence of such language suggests that “the documents appear to have been copied from an internal system or code repository and not directly accessed through external remote access or discovered on any external staging server.”
That would point the finger at a rogue insider rather than an external hacking crew, Flashpoint said.
The timing of the attack coincides with leaks by former Booze Allen Hamilton contractor Edward Snowden, but there has (as yet) been nothing linking Snowden to the theft of the hacking tools offered by The Shadow Crew. That could mean that there were “multiple insiders acting independently” within NSA around 2013, Flashpoint said.
