In-brief: Trend Micro argues that Internet of Things devices including connected vehicle and smart home products are a natural next step for ransomware scammers.
Trend Micro has an interesting blog post that delves into the (pertinent) topic of ransomware and connected devices. Trend asks whether the Internet of Things (IoT) may be the next frontier for cyber extortion via ransomware. The short answer might be “why not?”
From the article:
The Internet of Things (IoT)—the network of devices embedded with capabilities to collect and exchange information—has long been attracting the attention of cybercriminals as it continues to gain momentum in terms of its adoption…How can cybercriminals potentially take advantage of this?
Despite being equipped with new applications and hardware, most IoT devices are furnished with outdated connection protocols and operating systems (OS). Remotely controlled lightbulbs and WiFi-enabled In-Vehicle Infotainment (IVI) systems, for instance, are mostly run in Linux and developed in C language without safe compiler options. They also use dated connection protocols such as TCP/IP (1989, RFC 1122), ZigBee (2004 specification) and CAN 2.0 (1991), which when exploited can open up the device to remote access.
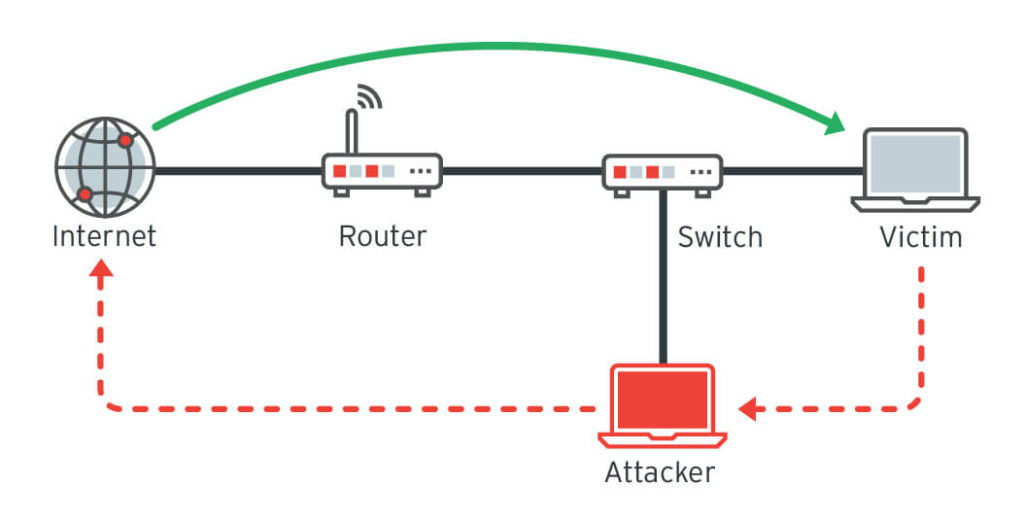
For instance, exploiting a TCP/IP protocol can lead to a man-in-the-middle attack where malicious third parties can tap into an IoT device’s network, intercept its traffic and ultimately gain access to the device.
That makes IoT devices particularly vulnerable to attack and compromise. How? Well, using the same techniques hackers leverage for access to non-IoT systems. Namely: using exploits or the default credentials to access the device, or compromising adjacent endpoints on a network and moving laterally to compromise IoT devices.
The difference comes in the final stages of the attack: using access for financial (or political) gain. IoT devices like connected homes and cars give attackers much more leverage than mere IT assets like laptops and servers. Disabling a car or interfering with a smart TV or home monitoring system are attacks that will be felt immediately and intimately. And, given that ransomware is all about the extortion, such schemes would seem to be more likely to result in pay-outs.
Of course, Trend doesn’t expect to see ransomware attacks on smart devices soon. But the company does consider it a trend worth watching and taking steps to mitigate. From their blog post:
The growing adoption of IoT devices, the relative ease of exploiting their security flaws and the seeming profitability of extorting their owners, are a daunting combination. And while there is no silver bullet for completely securing the vast network of connected devices, countermeasures such as implementing a security audit when designing IoT software/hardware, setting up security gateways, adding endpoint monitoring and utilizing real-time log inspection can help mitigate the risks.

The Internet is still not secure, so we can’t expect ”IoT” to be secure, either. However, security is constantly evolving to meet new challenges, we’ve seen it before, and we’ll see it again, with IoT and subsequent connected technologies.
Read this whitepaper :Interconnection of everything to get an overview of the technologies that enable the IoT and it explores the challenge of defining what the “Internet of Things” is.
This paper looked at why “IoT” can mean different things to different people.