In-brief: A vulnerability in software by device maker D-Link is much more widespread than initially believed, affecting hundreds of thousands of Internet connected devices, including cameras, home routers, wireless access points and network attached storage.
A vulnerability in software by device maker D-Link is much more widespread than initially believed, affecting hundreds of thousands of Internet connected devices, including cameras, home routers, wireless access points and network attached storage.
The security firm Senrio said on Thursday that a vulnerability it first disclosed in June in D-Link’s DCS-930L Network Cloud Camera also affects “a huge range of products” made by that company. More than 120 models across Connected Home Products, including cameras, routers, access points, modems, and storage, are affected by this single vulnerability, Senrio said in a statement.
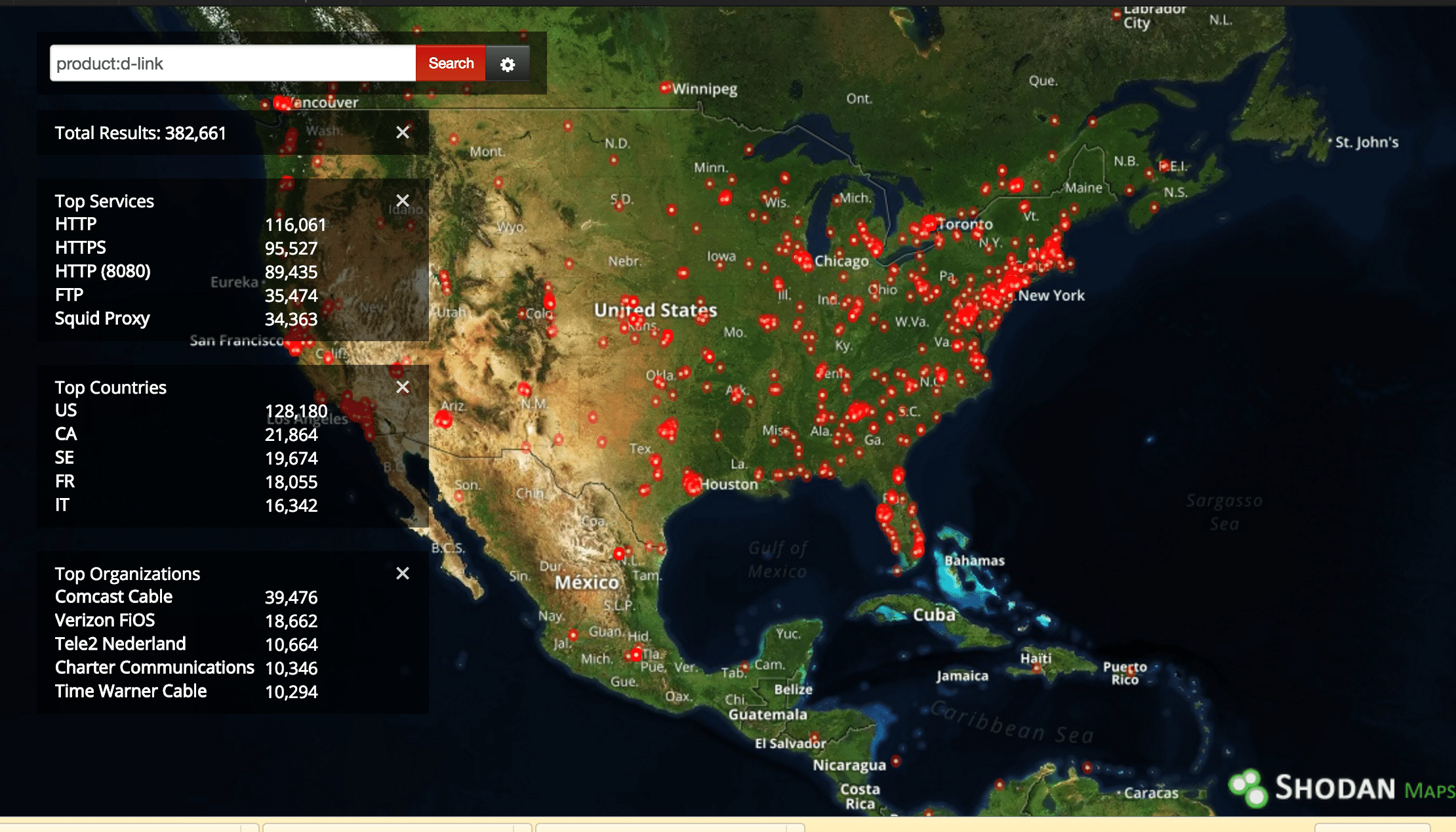
As many as 400,000 D-Link devices that are accessible from the public Internet are vulnerable to remote attack as a result of the remote code execution flaw, Senrio said. A search using the hardware search engine Shodan.io uncovered more than 120,000 D-Link devices deployed in the U.S. that could be accessed from the Internet.
D-Link has issued firmware updates in recent weeks to address the issues identified by Senrio. However, the flaws underscore the kinds of distributed risks that can result from vulnerabilities in common hardware and software components that may be used extensively within products by the same vendor, or different vendors, Senrio said.
The company first disclosed the flaw, described as a “Stack Overflow Loophole” on June 8, noting at the time that it could be used to remotely overwrite the device administrator password on D-Link DCS-930L Cloud Cameras, but that the flaw may also be much more widespread. At the time, Senrio estimated that around 50,000 publically addressable cameras were affected globally.

The flaw was in a service that processes remote commands. “The vulnerable function copies data from an incoming string to a stack buffer, overwriting the return address of the function,” Senrio noted. “This vulnerability can be exploited with a single command which contains custom assembly code and a string crafted to exercise the overflow.”
If successfully launched, an attack allows code injection to the vulnerable device, allowing the attacker to set a custom password, overwriting the user’s password and granting remote access to the camera feed. “Instead of setting a new password as the exploit, an attacker could just as easily add a new user with administrator access, download firmware or otherwise re-configure this device,” Senrio noted.
At the time, the company said it was likely the flaw extended far beyond D-Link’s Cloud Camera product line.
“Looking at the architecture of the product line and where the vulnerability was found in the software stack, the bug is likely not confined to a single model but prevalent in other products using the same sub-system,” the company said. “This vulnerability points to a bigger issue of poorly written firmware components used in cheap Systems on Chips (SoCs).”
In recent days, Senrio heard back from D-Link, which confirmed that the problem was, indeed, prevalent throughout D-Link’s connected products line. In recent days, D-Link has posted a notice to its support web site regarding the issue.
“D-Link is working to address the reported DCS-930L vulnerability,” the company said, noting that it”expects to release the updated DCS-930L firmware by Friday, July 15″ and that “additional testing is underway to confirm impact on any other D-Link models.”
D-Link has posted a string of firmware updates in the last two weeks for its DCS-model cameras, DNR line of network video recorders and DGS model switches to address the vulnerability.
The larger issue is one that affects both D-Link and other makers of Internet connected devices. Namely: supply chain risks emerge when a single software component gets reused throughout company product lines.
“This is the gospel we’ve been trying to preach especially to the industrial control folks who we see this pattern the most in,” said Stephen Ridley, co-founder of Senrio (formerly Xipiter).
Supply chain issues that affect low-cost gear used in homes and small businesses are nothing new. In August 2015, for example, Carnegie Mellon University’s CERT warned about a hard-coded firmware password that was known to affect DSL routers by the Chinese firm ZTE Corp, but actually affected a far wider range of devices, exposing them to remote compromise. DSL routers sold under the ASUS, DIGICOM, Observa Telecom and Philippine Long Distance Telephone (PLDT) were found to run the same firmware and to be affected by the same vulnerability.
