In-brief: Verizon said in its 2016 Data Breach Investigations Report that it found no “real world” data on cyber incidents tied to Internet of Things technologies. Really?
Verizon on Wednesday released its much anticipated Data Breach Investigations Report (or DBIR, as its known), one of the most comprehensive private sector reports on malicious activity targeting corporations.
Among the many conclusions and inferences drawn from the accounting of more than 64,000 security incidents and 3,000 data breaches was this: the Internet of Things isn’t a thing, at least as far as data breaches are concerned.

In fact, the Internet of Things is referenced just once in the 85 page report, with Verizon concluding that “we still do not have significant real-world data on these technologies as the vector of attack on organizations.” Organizations and individuals that have data on such incidents are invited to share it. “We are always looking for avenues to shine lights into areas in which we may not have sufficient illumination,” the report reads.
What the report does illuminate is a continuation of trends reported in prior years, with precious little evidence that the organizations who make up the DBIR – many in retail, healthcare, manufacturing and (especially) the public sector – are learning their lessons.
Phishing attacks continued to be the main avenue by which data breaches occurred. Verizon recorded 9,576 total incidents of phishing attacks. Of those, 916 – close to 10 percent – were linked to “confirmed data disclosure.” Studying a combined eight million results of sanctioned phishing tests in 2015 from multiple security awareness vendors aiming, Verizon found that 30% of phishing messages were opened by the target across all campaigns while 12% went on to click the malicious attachment or link and thus enabled the attack to succeed. That figure actually marks an increase from previous years (just 23% opened the e-mail in a 2015 test).
User credentials were the most common target of hackers. Credential theft was a component of 829 of 905 confirmed breaches that Verizon studied – possibly as a precursor to longer and more complex operations inside a breached firm.
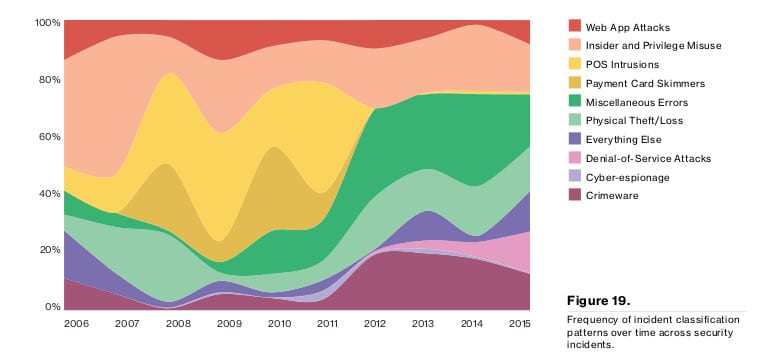
Web application attacks were a major trend in the last year, with attacks on content management systems (CMS) like Drupal and WordPress as a precursor to installation of web shells. Attackers frequently exploited holes like remote file inclusion vulnerabilities or abused insecure upload functionality to upload web shells that act as back doors to the environment on which the application runs. For example: in financially motivated attacks against e-commerce servers, web shells are used to access the payment application code, which is then modified with a new feature that will capture the user input (think payment card number and CVV) for future pickup, Verizon noted. SQL injection was also a common vector of attack for web applications, Verizon noted.
Attacks on Point of Sale systems continued to be a sore spot for companies, as did compromises by way of third party contractors and business partners, Verizon noted.
As in past years, the DBIR is prone to a kind of confirmation bias. Namely: the report and its conclusions are limited by the data that goes into the report itself. That means that trends (and conclusions about those trends) can vary widely from year to year, while excluding entire categories of threats simply because “the data is not there.”
Such may be the case with Internet of Things. After all, in a year that saw multiple reports about attacks on critical infrastructure as well as connected home platforms, simply concluding that there were no incidents linked to platforms that could broadly be considered “IoT” seems premature.
To its credit, the Verizon report notes that the absence of IoT data “is not a suggestion to ignore these areas in your risk management decision-making.” As we have seen, conclusions about the death or birth of particular security risks are often premature.

