In-brief: There are more warnings that a common piece of hardware known as Serial-to-Ethernet converters are very vulnerable to remote attacks – and more evidence that the vendors who manufacture them aren’t in a rush to fix the holes.
Months after unidentified hackers caused a massive power outage in the Ukraine, in part by attacking an unsexy category of devices known as Serial-to-Ethernet Converters, there are more warnings that these common pieces of hardware are very vulnerable to remote, online attack and compromise – and more evidence that the vendors who manufacture them aren’t in a rush to fix the holes.
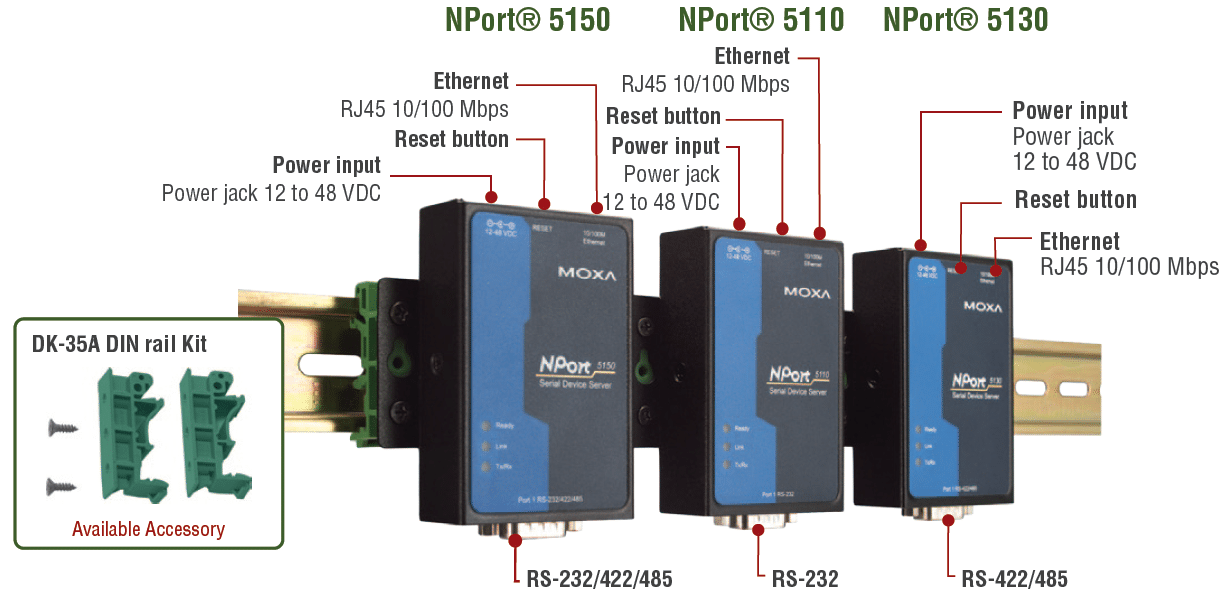
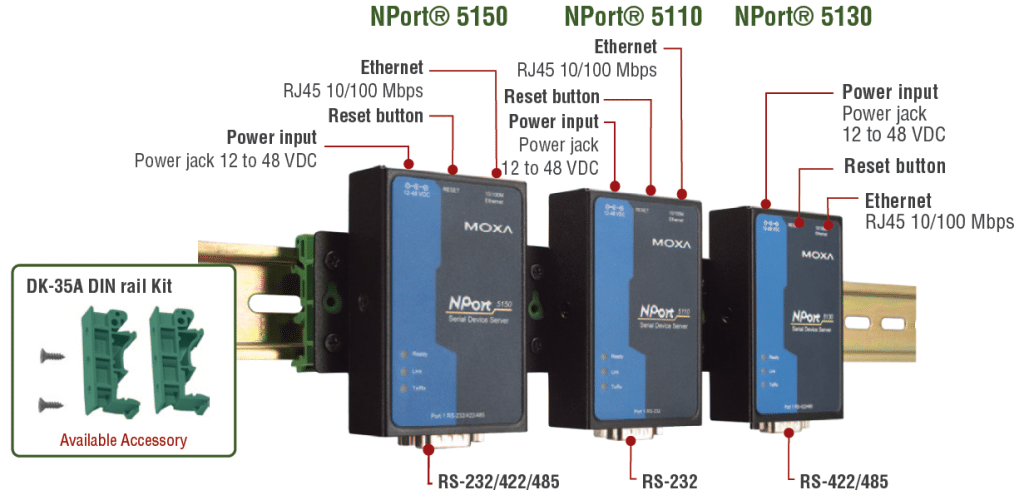
The latest evidence of this came last week, when the Department of Homeland Security’s Industrial Control System CERT (ICS CERT) issued an alert about one of the most commonly used serial to ethernet converters, a device called NPort and manufactured by a Taiwanese company, Moxa.
ICS CERT issued a security advisory on April 8, citing public reports of vulnerabilities affecting a range of Moxa NPort devices, including the 6110 Modbus/TCP to serial communication gateway and the 6000 and 5100 series serial to ethernet converters.
According to the ICS the Moxa devices contain a number of serious vulnerabilities including one that allows a remote attacker to retrieve sensitive information from the device, another that would permit an attacker to push new firmware (software) onto the converter, giving her total control over it, as well as a third buffer overflow vulnerability that opens the devices to having malicious code run on it. The attacks could be carried out without first authenticating to the vulnerable Moxa device, ICS-CERT warned.
[Read more Security Ledger coverage of threats to critical infrastructure.]
After conferring with the company, Homeland Security said this week that a patch will be available for two of the vulnerable devices…in late August. In the meantime, For customers using the NPort 6110, the advice from Moxa is to upgrade. “Moxa has reported that the Moxa NPort 6110 has been discontinued and will not have patches released to address these vulnerabilities. Moxa recommends that customers using legacy devices should upgrade the affected devices,” ICS-CERT said in its advisory.
The alert follows the release of an advisory by Joakim Kennedy of the firm Rapid7 on March 15th describing the issues. March 17 that detailed “scores” of vulnerabilities in Moxa devices. ICS-CERT said it is not aware of publicly available exploit code that exploits the identified vulnerabilities.
The warning is just the latest concerning serial to ethernet controllers, incredibly common pieces of equipment in everything from hospitals to critical infrastructure settings to corporate data centers.
Serial to Ethernet converters represent one of the single, biggest risks in the industrial control system sector, security experts agree. They “connect devices to the Internet that were never meant to be connected to the Internet,” said Billy Rios, a noted researcher and the CEO and founder of the firm Whitescope.
Serial communications ports were common on older generations of hardware (think: that old VGA monitor). As a result, serial communications protocols have few security protections. The assumption of those designing serial protocols and devices that use them was that anything connected to the same communications bus as the serial device is trusted, Rios said.
The devices are used widely. For companies running aging equipment that only supports serial communications, the Serial to Ethernet converters allow the devices to be managed remotely. They also translate older -but-common protocols like Modbus into TCP/IP, the lingua franca of the Internet.

Rios says that he has found the devices used across industries. He has seen them deployed on airplanes to help manage aging avionics systems. They’re very common in healthcare settings as well, where diagnostic equipment might have a useful life that is measured in decades. But the converters are also commonly found in data centers, to provide remote and low level management of critical systems. “If you’re a Fortune 1,000 company, you’ve got some of these,” Rios said.
But the devices’ lack of security is a big problem. Attackers who gain access to networked environments to which serial devices are attacked find that they can easily pivot to the device and exploit its lack of security to cause real-world impact, Rios said.
That was what happened in the recent attack on electrical utilities in Ukraine. According to a DHS report on that incident, the hackers “rendered Serial-to-Ethernet devices at substations inoperable by corrupting their firmware” – exactly the type of malicious action that the Rapid7 researchers warn could happen with the Moxa devices.
For malicious actors, taking control of the Serial to Ethernet converter is paramount controlling the devices that connect to it, experts said “Once you have access to the converter, its game over,” said Rios. “The devices attached to it will do whatever you tell them to do.”
Warnings about the devices aren’t new. Researchers at the firm Digital Bond and other firms have been testing Serial to Ethernet controllers – Moxa’s included- since 2012 years and have warned repeatedly that the devices lack many security protections common in other connected systems.
Wightman said that he and other researchers have shared the findings of their independent work with the affected vendors, including Moxa, to little effect.
“They’ll say ‘OK. Thanks for the info. We’ll figure something out,’ and then they’ll drop it,” he said.
Moxa is a Taiwan-based company whose products are widely used. A search of the Internet using the Shodan search engine, for example, reveals more than 5,100 Internet accessible devices, including many different NPort models.
The ICS-CERT advisory marks progress of a sort. In a recent advisory, prior to the release of the ICS CERT advisory, Digital Bond Wightman noted that it contacted Moxa about vulnerabilities in its products in July, 2015 and has had “repeated contact” with the company over six months, but the company has not addressed the issues. All the units tested by the firm were still vulnerable using the most up to date firmware in April, 2016.
“It does not appear that Moxa intends to address these security issues in its products,” he wrote.
Still, the company has only pledged to address the known security issues. However, Wightman said that more, as-yet-undiscovered holes likely exist.
“I haven’t encountered a serial converter yet that is very secure,” said Reid Wightman, the Director at Digital Bond labs. “We’ve always told customers to treat these products as if they’re totally vulnerable to anything.”
Rios agreed. “Companies have to start doing their own testing of these products,” he said. “You can’t rely on the vendor. You have to manage these as if they belong to you. Waiting six or seven months for a critical patch? You can’t do that. You’ve gotta lock these down.”