
In-brief: A highly ranked web application for sharing tales of infidelity is the beneficiary of a sophisticated, global campaign of malicious search engine optimization (SEO), according to Akamai Principal Security Researcher Or Katz. (Read more stories by Or here.)
Search Engine Optimization (SEO) campaigns are prevalent and legitimate ways to promote Web applications in order to get a better visibility and more traffic to your Web application. But what happens when an SEO campaign crosses the line into the dark side and becomes malicious?
Recently the Akamai Threat Research Team discovered a highly sophisticated SEO attack campaign that was promoting the search results rating for a Web application that allows users to share their cheating and infidelity stories.
[Read more Security Ledger coverage of SEO type attacks.]
The complexity of this attack campaign included defacement of hundreds of Web applications across the Internet by abusing vulnerable Windows Web servers and injecting HTML links – using an SQL injection technique. By injecting reference links between the defaced applications to the “cheating stories” application, the attackers tried to mimic normal distribution of content over the Web. Once the injected content is placed, the attacker counts on the scanning that search engines perform to determine what should be the best results for any given keywords. As a result, the rating of the “cheating stories” application will be calculated based on the quality and quantity of those links.
This article reveals the details and findings of the targeted SEO attack, including the end result: The “cheating stories” application being highly ranked by the leading search engines.
Anatomy of the Attack
By analyzing Internet traffic data on the Akamai Intelligent Platform for one month, the Threat Research Team was able to detect two weeks of distributed attack activity where attackers targeted more than 3,500 Windows Servers Web applications.
In this attack, the attackers attempted to inject malicious content to Web Application Databases by sending SQL injection payloads that contained HTML links. In order to execute this campaign and mask their identity, the attackers used a Botnet of over 300 IP address from all over the world.
In this case, the goal of the attack was merely to drive traffic to the application in question. So the outcome of a successful attack resulted in Web application defacement by referring links. But it could have easily injected malicious javascript code that targeted Web application users or even leaked sensitive database content.
Why the attack worked
Search engines consider many factors to determine search results ranking. For example: the number of links redirecting to the Web application and the reputation of the referring links (or Web applications) influences the rank of the site in question. This is the basis for “Page Rank,” the original brains behind the Google search engine. But while most of the elements that affect a page’s rank are well-known, the exact recipe – or combination of those factors into the search engine ranking formula – is a big mystery.
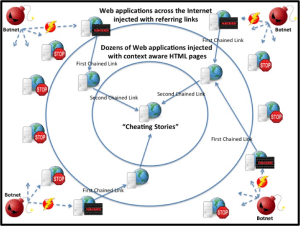
In this case, attackers used a number of search engine optimization techniques mimic Internet content and make sure it will be factored properly by search engines. These include:
+ Chain of links redirection: The attacker created a chain of external links leading to the “cheating stories” Web application.
The first chained link was created by the SQL injection Botnet attack, injecting HTML links into as many Web applications as possible across the Internet. In the entire attack campaign, dozens of referring links to Web applications were used – none of which are the “cheating stories” Web application. The second chained link was from those dozens Web applications that contain context aware HTML pages to the target of the SEO campaign, which is the “cheating stories” Web application.
While there hasn’t been evidence of that, it is expected that dozens Web applications were also a victim of defacement. It is assumed that the chaining of links is done in order to mimic normal distribution of content over the Web in a way that will lead search engines to see it as legitimate content.
+ Context awareness: Since the Web application that was promoted via the “cheating” business, we can see link anchor text, the text used on a hyperlink, content and comments that use words such as: husband, cheat, affairs, women, etc. This usage of keywords plays hand-in-hand to the way that search engines algorithms do their job and map keywords to the relevant pages. Figure 2: Example for page content of the second link in the chain, leading to the “cheating stories” Research also indicated that the attackers created content that emphasized the relevant context by implanting meaningful content inside meaningless content (as seen in the figure below).

Postmortem Analysis
As part of the attack postmortem analysis, the following findings were revealed:
- Evidence of mass defacement – when searching the Internet for the HTML links that were used as part of this campaign, hundreds of Web applications contained malicious links
- Leading search engines – when searching for a combination of common words such as “cheat” and “story”, it was apparent that the “cheating stories” application appeared on the first returned page of the leading search engines
- Web application analytics – looking at Alexa analytics, the ranking of the “cheating stories” application dramatically increased in the past three months
This campaign illustrates the level of sophistication attackers are using in order to promote Web applications, including malicious techniques such as: SQL injection, distributed botnet attacks, defacement and search engine optimization (SEO) attacks. Attackers showed a deep understanding of search engine algorithms, mimicking the normal distribution of content over the Web. The outcome of this attack campaign is clear: the “cheating stories” Web application is highly ranked by leading search engines.
Conclusions:
The search engine economy is built on the concept of visibility and exposure to Internet content. Simply put: a high search engine ranking can translate into significant revenue. In order to mitigate vulnerable Web application, Akamai recommends patching the vulnerability and using a Web Application Firewall (WAF) to protect against present and future SQL Injection attacks.
Detecting highly scaled, distributed attack across the Internet is much easier when done in a cloud network. Having the knowledge of such attack campaigns can be used as an actionable insight for improving mitigation for future attack campaigns.

I remember that spammer have no religion, I posted same comment on Akamai and strongly believe that Blackhat SEO is never die, we have discussed about it last week at http://www.adelaideseoservices.net.au Smarter people do it because of their job, we really go for improve our strategy as it think 🙂