A strong counter-narrative to the official account of the hacking of Sony Pictures Entertainment has emerged in recent days, with the visage of the petulant North Korean dictator, Kim Jong Un, replaced by another, more familiar face: former Sony Pictures employees angry over their firing during a recent reorganization at the company.
Researchers from the security firm Norse allege that their investigation of the hack of Sony has uncovered evidence that leads, decisively, away from North Korea as the source of the attack. Instead, the company alleges that a group of six individuals is behind the hack, at least one a former Sony Pictures Entertainment employee who worked in a technical role and had extensive knowledge of the company’s network and operations.
[Read Security Ledger coverage of the hack of Sony Pictures Entertainment.]
If true, the allegations by Norse deal a serious blow to the government’s account of the incident, which placed the blame squarely on hackers affiliated with the government of the Democratic Peoples Republic of Korea, or DPRK. That accusation, first aired last week, has been the source of heated rhetoric from both Washington D.C. and Pyongyang, the North Korean capital.
Speaking to The Security Ledger, Kurt Stammberger, a Senior Vice President at Norse, said that his company identified six individuals with direct involvement in the hack, including two based in the U.S., one in Canada, one in Singapore and one in Thailand. The six include one former Sony employee, a ten-year veteran of the company who was laid off in May as part of a company-wide restructuring.
Stammberger said that Norse’s team of around nine researchers started from the premise that insiders would be the best situated to carry out an attack on the company and steal data. The company analyzed human resources documents leaked in the hack and began researching employees with a likely motive and means to carry out a hack.
That HR data was the “golden nugget” in the investigation, revealing the details of a mass layoff at Sony in the Spring of 2014, including a spreadsheet identifying employees who were fired from Sony Pictures in the April-May time period.
After researching those individuals, Norse said it identified one former employee who he described as having a “very technical background.” Researchers from the company followed that individual online, noting angry posts she mad e on social media about the layoffs and Sony. Through access to IRC (Internet Relay Chat) forums and other sites, they were also able to capture communications with other individuals affiliated with underground hacking and hacktivist groups in Europe and Asia.
According to Stammberger, the Norse investigation was further able to connect an individual directly involved in those online conversations with the Sony employee with a server on which the earliest known version of the malware used in the attack was compiled, in July, 2014.
Stammberger was careful to note that his company’s findings are hardly conclusive, and may just add wrinkles to an already wrinkled picture of what happened at Sony Pictures. He said Norse employees will be briefing the FBI on Monday about their findings.
“They’re the investigators,” Stammberger said. “We’re going to show them our data and where it points us. As far as whether it is proof that would stand up in a court of law? That’s not our job to determine, it is theirs,” he said of the FBI.
At a minimum, the latest theory suggest that official accounts of the hack from U.S. government sources are now just one among many competing theories about the source of motivation behind the attack that are circulating within security circles and in the mainstream media. This, ten days after the Obama Administration pinned the blame for the destructive attack squarely on hackers affiliated with the reclusive government of the Democratic Peoples Republic of Korea (DPRK).
The sheer amount of information leaked by the hackers has provided plenty of ammunition to fuel alternative narratives about what happened. Initial reports noted that the malware used in the attacks on Sony was created on systems that used Korean language software libraries, and shared similarities with malicious software used in destructive attacks on the Saudi oil firm Saudi Aramco.
But for every clue that seems to point to the involvement of the DPRK, there are others that point in other directions, as well. For example, recent analysis has focused on date and time stamps attached to the leaked Sony data. Researchers have used those time stamps to infer the speed with which the data was transferred off Sony’s network. Reports have suggested that the timestamp data points to a data leak within Sony’s enterprise network, for example: to a USB device or external hard drive.
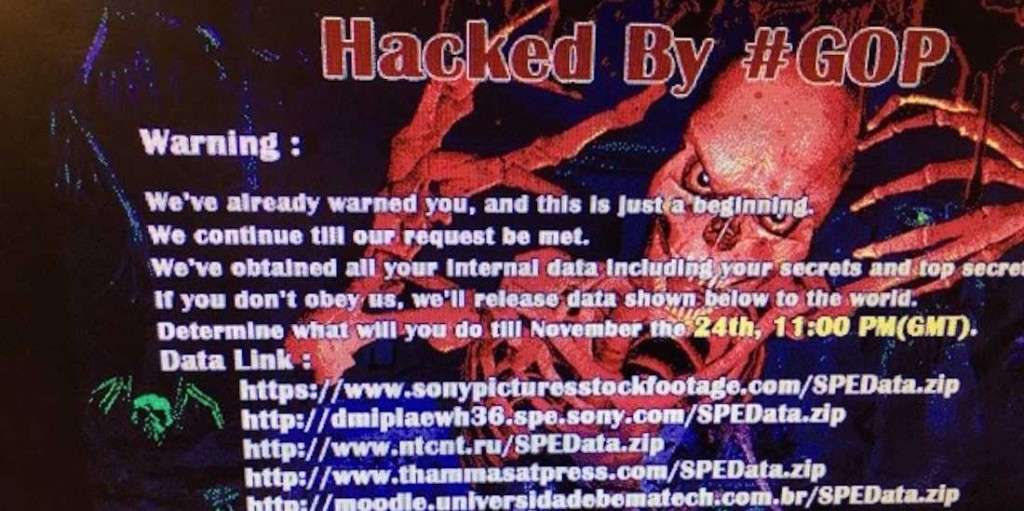
Other analysis studied clues buried in statements made by the shadowy hacking crew, the Guardians of Peace or GOP, who claimed responsibility for the attacks. Email addresses and other ephemera from the GOP communications with Sony and the outside world have been read to reveal links to everything from Japanese anime and the Mighty Morphin Power Rangers television show to U.S. domestic disputes over politics and gender equality. Further, linguistic analysis of GOP’s online communications suggests they were penned by someone who is a native Russian speaker, not a native Korean (or English) speaker.
But the Norse account of the hack does answer some puzzling questions about the incident that are as yet unexplained, according to Mark Rasch, a former federal prosecutor and a principal at Rasch Technology and Cyberlaw. Among those questions: how hackers were able to obtain near-perfect knowledge of Sony Pictures’ network and, then, sneak terabytes of data off of the network without arousing notice.
“It has always been suspicious that it was North Korea,” Rasch said. “Not impossible – but doubtful…It made a lot more sense that it was insiders pretending to be North Korea.”
Rasch noted, as others have, that the attackers initially made no mention of the Sony Pictures film “The Interview” in communications with the company or the outside world. Rasch notes that the hackers also exhibited a somewhat sophisticated knowledge of how Hollywood works – leaking data that was deeply personal and particularly embarrassing to Sony executives.
Stammberger notes the involvement of an insider would explain how the attackers obtained critical information about Sony’s network, including the IP addresses of critical servers and valid credentials to log into them. Even in sophisticated attacks, remote actors might spend days, weeks or months probing a network to which they have gained access to obtain that information: using compromised employee accounts to explore and find sensitive data before stealing it or causing other damage. It is during that “lateral movement,” malicious actors are often spotted, Stammberger said. In the case of the Sony hack, however, the malware was compiled knowing exactly what assets to attack.
Still, there are many questions that have yet to be answered. Norse’s own analysis has plenty of blank spaces. Stammberger said that a “handful” of former employees may have been involved, though only one was linked directly to the hack. That employee, at some point, joined forces with external actors and more experienced hackers with a grudge against Sony, including individuals involved with sites like the Pirate Bay which offer Hollywood movies for download. “We see evidence for those two groups of people getting together,” Stammberger told The Security Ledger.

Pingback: » Sony Hack: New Evidence Points to Inside Job Say Security Experts AUDIO KORNER
Pingback: FBI stands firm on North Korea as doubts surface over who hacked Sony – Charlotte Observer | Superior News Update
Pingback: Security Experts Doubt North Korea Role in Sony Hacking Attack | Variety
Pingback: FBI Busted Falsely Blaming North Korea for Sony Hack | peoples trust toronto
Pingback: FBI Busted Falsely Blaming North Korea for Sony Hack | ZombieMarkets
It was a publicity stunt for a mediocre film, people…
Or are you too young to remember when Martians landed in New Jersey?
SONY should be held accountable to the taxpayers for creating an costly international incident just to prevent a box office embarrassment!
Sony will suffer $100m in damages. How is this a publicity stunt? Also, as our CEO said, it was a RAT (remote access trojan). Norse tracks external packets, FBI, Mandiant have internal knowledge about the breach. All the rest is speculation. Please learn about RATs – once infected you become the ‘malicious’ insider when you’re a non-malicious employee. Check your smartphone and you’ll see one or more of your free apps is a RAT. Just read the permissions and you’ll see. Trace some packets and decompile the code. You’ll see. support@snoopwall.com
I realize it’s difficult for people who don’t live here to grasp how it works in this town.
Hollywood is about the business of making box office profits, not the art of the moving picture, and certainly not the idealism of social morality.
So, SONY claims this cost them $100M, huh? Can someone show me where?
Pascal is now a “media star” (The Wrap); none of the 5 films that were supposedly “hacked” can be found on the common torrent sites, so they’re not losing any box revs; a film that would have been lucky to break $5M (they knew this from pre-release test audience studies) has now racked up $17M and counting…
You can get some perspective on the benefits SONY has reaped from the “damages” it has “suffered” here: (http://deadline.com/2014/12/sony-fury-annie-piracy-facebook-youtube-1201305353/)
SONY is far from “hurting” over this. Movies have as big a promotion budget as they do a production budget, often larger. Without spending one thin dime, SONY reaps millions in free publicity for content their marketing staff already knew was a flop.
The hack reportedly provided complete access to SONY’s core, but only grabbed some emails, a few salary records, and 5 movies… No top-sheets, no budget records, no other accounting records…none of the stuff their accountants don’t want the tax man examining too closely… nothing that could actually hurt the studio.
As to the “leaked” emails… Can you believe Hollywood is full of two-faced, backstabbing, name-calling studio execs? Who’d have thunk?
Did Angie, or anyone else, grab a lawyer and sue for slander or break their contract with SONY over these “highly inflammatory” emails? Anyone?
Is Pascal’s or Rudin’s job on the line for making racist remarks in private communication? Or is corporate discipline limited to NBA franchise owners?
And since when have studio heads had an issue with bragging about their wealth?
Has the IRS bothered to check if what they put on their tax forms matches what SONY’s records reflect? In my forty plus years of experience in the entertainment industry, this is a far more plausible basis for their after-the-fact concern.
Regarding the FBI… The plutocracy we live in is looking for any excuse to justify a state of “perpetual war”! Anything that comes from the FBI, CIA or NSA is Machiavellian at best!
Ask yourself… What would happen if the FBI (or Norse and Mandiant for that matter) admitted they’d been duped by a major studio? Public confidence in the government and it’s corporate buddies & bankers is at an all-time low already, so… blame the Norks… someone we, the general public, aren’t allowed to communicate with and check the facts.
Trojans are commonplace, as you point out, but this also makes them easily detectable by most AV software, and Trojans are certainly simple enough to inject in a system to give the appearance of an intrusion. Most high-school students can demonstrate this.
A worm would have been a more effective tool, any hacker with half a brain knows this… ask the Russians, Israelis, or Chinese (the top three cyber-espionage offenders of US internet security, according to the Fed). Cyber-security experts know this, and yet continue to support this indictment of NK. Self-preservation.
I don’t believe the marketing team at SONY set out intending to create an international incident, it was a buzz generating gimmick which escalated out of control. The viral age has thorns.
Now that it has escalated, there’s the overwhelming odor of an elephant with an erection, not a RAT.
Maybe after all my years working in Hollywood I have become jaded, but this had publicity stunt written all over it from the start!
Thank you.
I’ve been saying the Sony Pictures Entertainment marketing dept. played our President since it happened.
Well said.
Not a publicity stunt when terabytes of confidential company data are stolen and released on the Internet. it wasn’t as if a select group of emails were stolen, the entire email spool of the head of the studio was stolen including every word ever written in email – 90% of which were previously protected by law as confidential company property. Virtually every piece of data on file shares was stolen. Sorry, this didn’t cost Sony Pictures $100M, it cost them a whole lot more. This was a massive breach of corporate confidentiality, likely unprecedented, and no one in any business even Hollywood could justify the impact to former and current employee confidentiality for the sake of what equated to a silly stoner movie; the people who initiated this wanted to damage Sony Pictures in an epic way, and were not afraid of the repercussions, likely because they do not live in th US and won’t face our laws.
I have cited hard numbers to demonstrate how SONY profited from this. You, on the other hand, disagree but cite no data to back your position. Not much of an argument.
Secondly, there’s no such thing as “confidential company data”… Ever hear of ECHELON? The NSA, FBI, and CIA know what you think, what you eat, what you wear, and what particular flavor of porn you consume.
Then they took your Facebook photo and plugged it into their facial recognition system so they can track you on so-called “security cameras” as you move about any metropolitan area of the country!
If people really understood how much “privacy” they traded for a Star Trek communicator, they’d throw away their cell phones.
Corporate greed runs Hollywood. Eyeballs are the only thing important here, and capturing those eyeballs has been justification enough for any number of sins for decades. Time to take off those rose-colored glasses.
Yeah – I think we can safely rule out “publicity stunt.” I think, with PR as in medicine, the rule is “first, do no harm.” I really don’t see how the plan to ‘release all our corporate data to generate controversy and get people into the theater’ wouldn’t have gotten anyone proposing it fired on the spot. Talk about overkill! The question really is between “DPRK” (the government’s contention) and “disgruntled employee/former employee working with hacktivists” (the contention of Norse and some other security firms.)
“I think, with PR as in medicine, the rule is “first, do no harm.” ”
My friend, that is simply naive. “Independence Day” pulled almost exactly what Wells did in ’38, mounting a 30 minute fake “news program” over the FOX networks… with precisely the same result!
911 was inundated with calls about the “invasion”… tying up phone lines, and preventing emergency services from responding to actual emergencies in a timely manner. How many people’s homes burned to the ground when the fire trucks could have been there in time… how many people died in the twisted steel of their car while paramedics were unable to receive the call… no one will ever know, count, or care. The film grossed a record-setting billion dollars at the box office… Do no harm.
Blair Witch, House of Wax (2005, “See Paris Hilton Die!”), Balloon Boy, the list goes on.
And it’s not new… In 1890 A guy got the bright idea to crash two fully-loaded trains into each other. Folks actually clamored for the chance to be passengers. Needless to say, the result was death and injury, but for a short time Crush, Texas was the second largest city in the great state of Texas… so it was worth it, right?
Now if you really think the medical industry believes in their oath, then you don’t understand the relationship between Big Pharma and Obamacare. Ask your doctor how much of a bonus he gets for every patient he puts on statins. Or for every smoker he signs up for Chantix, which was taken off the market by the FDA due to it killing users faster than the tobacco, then six months (and some surreptitious “lobbying”) later, there it is, right back as the go-to remedy for tobacco addiction, still killing people. Do no harm.
If you’re out to make people believe you’ve been hacked, you add select “corporate data” to the list of “violated” properties… just enough to make it believable… the fact remains, if “all our corporate data” had been released, the public would have a clear picture of how major studios “pad” budgets, juggle “vendor” fees through wholly owned foreign subsidiaries, manipulate union “incentives”, etc., just to increase profits and avoid paying their fair share of taxes on those hundred million dollar box offices. Great actors, great directors, great producers… greater accountants… Hollywood.
I suffer no delusions about the business I’m in.
The only redeeming thing in this fiasco is that we now can lay into the Norks with drones and don’t have to sacrifice over a hundred thousand of our sons and daughters in a fight we don’t like to admit we didn’t win last time.
Thank you.
P.S. I can’t stop myself from thinking, that your name may rhyme with Buck.
Tinhat alert. Also, I would hazard a guess that there are very few here who remember a 1938 radio broadcast.
If it was a publicity stunt then what explains the takedown of the North Korean internet and cell phone networks?
Sony went about things wrong but the us government are the ones who got involved and started pointing fingers. Obama and his administration made us, the U.S. Look like fools.
Publicity stunt for Norse
Pingback: Sony hack: sacked employees could be to blame, new research claims | Stop Making Sense
Pingback: Infomania MagazineNew Research Blames Insiders, Not North Korea, for Sony Hack
Pingback: ste williams – NORKS? Pffft. Infosec bods blame disgruntled insiders for savage Sony hack
Pingback: New research claims that North Korea was not behind the Sony hack | Rare
Pingback: New research claims that North Korea was not behind the Sony hack | Slantpoint Libertarian
Pingback: Were malicious insiders to blame for Sony hack? - IT Manager Daily
So how come it takes so long to start exploring , and finding evidence for, alternatives to the initial hack? It took about a week after the release of the ‘big 5’ Sony movies to the leak of the email and the almost instantaneous announcement that the ‘norks’ did it to stop the release of what appears to be a real dud.
Here we are two weeks later finding things that seem to indicate that the sleuths who hit the media first might be real investigative lightweights.
Pingback: What Happens If It Turns Out North Korea Had Nothing To Do With The Sony Hack? | We Minored In Film
Pingback: Sony Hack: One of the Greatest Publicity Stunts Ever?
Pingback: Sony Hack: New Evidence Points to Inside Job, Security Experts Say | USA Star
Pingback: Sony Hack: New Evidence Points to Inside Job, Security Experts Say | usa entertainment
Pingback: The World – Sony Hack An Inside Job?
Pingback: 罗生门?新证据显示,索尼被黑或与朝鲜无关【快鲤鱼早报】 | 23Seed
Pingback: FBI Spurns Evidence on Sony Hack, Blames North Korea Again -- News from Antiwar.com
Pingback: Sony Hack: FBI Doubles Down on North Korea Blame Amid New Doubt from Experts - Trendingnewsz.com
The premise of starting from an inside job is equivalent to the local police looking at the boyfriend when a girl is murdered. It’s about the averages and common motives. Makes sense and what is enlightening is while they do not claim to have the whole truth, the people criticizing this approach seem to be very upset. Methinks they doth protest too much… No, it doesn’t prove anything, but it seems more plausible than the government of NK doing it.
Pingback: Sony Hack: New Evidence Points to Inside Job, Security Experts Say |
Pingback: So The Cyber Attack On Sony Pictures Was An Inside Job? | Rama's Screen
Pingback: 罗生门?新证据显示,索尼被黑或与朝鲜无关【快鲤鱼早报】 - 18kr.com - 关注移动互联网,智能手机,智能手环
Pingback: 罗生门?新证据显示,索尼被黑或与朝鲜无关【快鲤鱼早报】
Pingback: FBI Busted | Michigan Standard
very insightful
Pingback: Sony hack: sacked employees could be to blame, researchers claim | The Today Online
Pingback: FBI Busted Falsely Blaming North Korea for Sony Hack
Pingback: Nordkorea, Sony Pictures und wie Realität den Film überholt
Pingback: Sony Dusted Off Old BlackBerrys After Hack – PC Magazine | Everyday News Update
Pingback: The Interview Debacle: New Evidence Shows N. Korea Didn’t Hack Sony «
Pingback: FBI Busted Falsely Blaming North Korea for Sony Hack | Eyes Open Report
Pingback: Security Experts Believe Former Sony Employee, Not North Korea, Behind Breach | WebSpace Reviews
Pingback: Two Step: FBI Says DPRK Acted Alone, Had Help | The Security Ledger
Pingback: FBI Busted Falsely Blaming North Korea for Sony Hack - The Daily Rapid
Pingback: FBI Still Standing By Its ‘North Korea Did It!’ Claims On The Sony Hack | Technology
Pingback: Another War Party Proganda Scam: The Sony Hack Fraud | David Stockman's Contra Corner
To Whom This May Concern:
I would like to get confirmation that you got a story that is true. I would also like to know more about this one Canadian that was involved. Thank-you for telling this and wish that North Korea might not be involved. I find this interesting on how this is only coming out now. Just a couple of days after Christmas Eve and Christmas Day.
I know you must get a lot of emails. But, I am asking that you get back to me on this one. It is kind of important if you can.
Thank-you,
Jeffery G. Tunney
Pingback: Sony hack: sacked employees could be to blame, researchers claim | InfoClose
Pingback: Cyber security firm blames insiders for Sony hack | Cyber Security World
Pingback: FBI Still Standing By Its 'North Korea Did It!' Claims On The Sony Hack - Trendingnewsz.com
Pingback: Siti Internet Aziendali » Sony Pictures, un intreccio da sbrogliare
Pingback: Sony Hack: One Of The Greatest Publicity Stunts Ever? | Revere Radio Network
Pingback: Maybe North Korea Didn’t Hack Sony
Pingback: thegeeksreadinglist
Pingback: Obama Sanctions North Korea, Citing Discredited Sony Allegation -- News from Antiwar.com
Pingback: U.S. Sanctions 10 North Koreans In Sony Hack, Keeps Mum on Evidence | The Security Ledger
Pingback: Obama administration: North Koreans probably not responsible for Sony Hack, but hey, let’s sanction them anyway | From the Trenches World Report