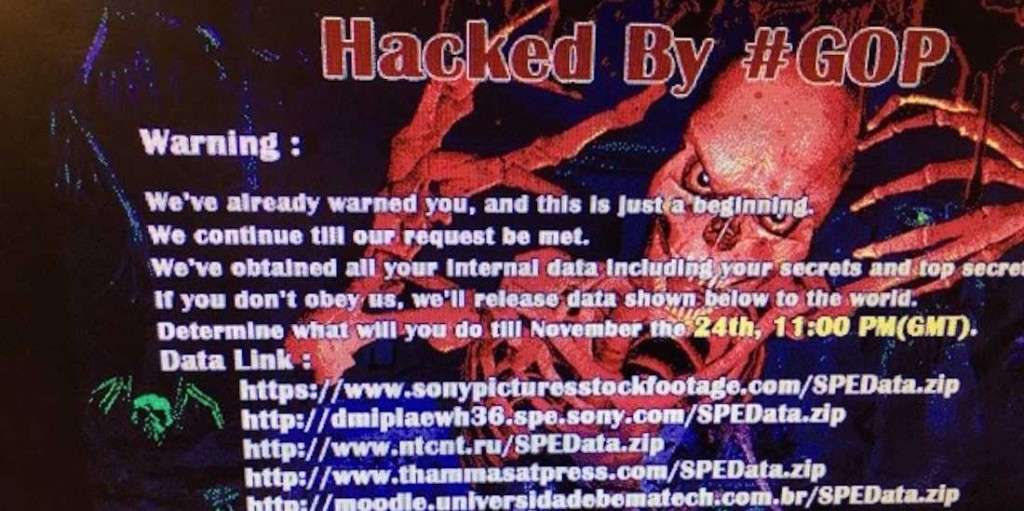
A strong counter-narrative to the official account of the hacking of Sony Pictures Entertainment has emerged in recent days, with the visage of the petulant North Korean dictator, Kim Jong Un, replaced by another, more familiar face: former Sony Pictures employees angry over their firing during a recent reorganization at the company.
Researchers from the security firm Norse allege that their investigation of the hack of Sony has uncovered evidence that leads, decisively, away from North Korea as the source of the attack. Instead, the company alleges that a group of six individuals is behind the hack, at least one a former Sony Pictures Entertainment employee who worked in a technical role and had extensive knowledge of the company’s network and operations.
[Read Security Ledger coverage of the hack of Sony Pictures Entertainment.]
If true, the allegations by Norse deal a serious blow to the government’s account of the incident, which placed the blame squarely on hackers affiliated with the government of the Democratic Peoples Republic of Korea, or DPRK. That accusation, first aired last week, has been the source of heated rhetoric from both Washington D.C. and Pyongyang, the North Korean capital.
Speaking to The Security Ledger, Kurt Stammberger, a Senior Vice President at Norse, said that his company identified six individuals with direct involvement in the hack, including two based in the U.S., one in Canada, one in Singapore and one in Thailand. The six include one former Sony employee, a ten-year veteran of the company who was laid off in May as part of a company-wide restructuring.
Stammberger said that Norse’s team of around nine researchers started from the premise that insiders would be the best situated to carry out an attack on the company and steal data. The company analyzed human resources documents leaked in the hack and began researching employees with a likely motive and means to carry out a hack.
That HR data was the “golden nugget” in the investigation, revealing the details of a mass layoff at Sony in the Spring of 2014, including a spreadsheet identifying employees who were fired from Sony Pictures in the April-May time period.
After researching those individuals, Norse said it identified one former employee who he described as having a “very technical background.” Researchers from the company followed that individual online, noting angry posts she mad e on social media about the layoffs and Sony. Through access to IRC (Internet Relay Chat) forums and other sites, they were also able to capture communications with other individuals affiliated with underground hacking and hacktivist groups in Europe and Asia.
According to Stammberger, the Norse investigation was further able to connect an individual directly involved in those online conversations with the Sony employee with a server on which the earliest known version of the malware used in the attack was compiled, in July, 2014.
Stammberger was careful to note that his company’s findings are hardly conclusive, and may just add wrinkles to an already wrinkled picture of what happened at Sony Pictures. He said Norse employees will be briefing the FBI on Monday about their findings.
“They’re the investigators,” Stammberger said. “We’re going to show them our data and where it points us. As far as whether it is proof that would stand up in a court of law? That’s not our job to determine, it is theirs,” he said of the FBI.
At a minimum, the latest theory suggest that official accounts of the hack from U.S. government sources are now just one among many competing theories about the source of motivation behind the attack that are circulating within security circles and in the mainstream media. This, ten days after the Obama Administration pinned the blame for the destructive attack squarely on hackers affiliated with the reclusive government of the Democratic Peoples Republic of Korea (DPRK).
The sheer amount of information leaked by the hackers has provided plenty of ammunition to fuel alternative narratives about what happened. Initial reports noted that the malware used in the attacks on Sony was created on systems that used Korean language software libraries, and shared similarities with malicious software used in destructive attacks on the Saudi oil firm Saudi Aramco.
But for every clue that seems to point to the involvement of the DPRK, there are others that point in other directions, as well. For example, recent analysis has focused on date and time stamps attached to the leaked Sony data. Researchers have used those time stamps to infer the speed with which the data was transferred off Sony’s network. Reports have suggested that the timestamp data points to a data leak within Sony’s enterprise network, for example: to a USB device or external hard drive.
Other analysis studied clues buried in statements made by the shadowy hacking crew, the Guardians of Peace or GOP, who claimed responsibility for the attacks. Email addresses and other ephemera from the GOP communications with Sony and the outside world have been read to reveal links to everything from Japanese anime and the Mighty Morphin Power Rangers television show to U.S. domestic disputes over politics and gender equality. Further, linguistic analysis of GOP’s online communications suggests they were penned by someone who is a native Russian speaker, not a native Korean (or English) speaker.
But the Norse account of the hack does answer some puzzling questions about the incident that are as yet unexplained, according to Mark Rasch, a former federal prosecutor and a principal at Rasch Technology and Cyberlaw. Among those questions: how hackers were able to obtain near-perfect knowledge of Sony Pictures’ network and, then, sneak terabytes of data off of the network without arousing notice.
“It has always been suspicious that it was North Korea,” Rasch said. “Not impossible – but doubtful…It made a lot more sense that it was insiders pretending to be North Korea.”
Rasch noted, as others have, that the attackers initially made no mention of the Sony Pictures film “The Interview” in communications with the company or the outside world. Rasch notes that the hackers also exhibited a somewhat sophisticated knowledge of how Hollywood works – leaking data that was deeply personal and particularly embarrassing to Sony executives.
Stammberger notes the involvement of an insider would explain how the attackers obtained critical information about Sony’s network, including the IP addresses of critical servers and valid credentials to log into them. Even in sophisticated attacks, remote actors might spend days, weeks or months probing a network to which they have gained access to obtain that information: using compromised employee accounts to explore and find sensitive data before stealing it or causing other damage. It is during that “lateral movement,” malicious actors are often spotted, Stammberger said. In the case of the Sony hack, however, the malware was compiled knowing exactly what assets to attack.
Still, there are many questions that have yet to be answered. Norse’s own analysis has plenty of blank spaces. Stammberger said that a “handful” of former employees may have been involved, though only one was linked directly to the hack. That employee, at some point, joined forces with external actors and more experienced hackers with a grudge against Sony, including individuals involved with sites like the Pirate Bay which offer Hollywood movies for download. “We see evidence for those two groups of people getting together,” Stammberger told The Security Ledger.

Use http://en.wikipedia.org/wiki/Occam%27s_razor – understand “the year of the RAT” http://www.snoopwall.com/2015-the-year-of-the-rat-threat-report/ any good insider becomes an accidental malicious insider by way of zero-day malware RATs. It’s that simple.
Gary,
I read your report in detail and couldn’t agree more with the comments that your “Threat Report” is “typical white paper drivel.”
1. The use of Occam’s Razor here is just WRONG! In your “Threat Report”, your parsimonious reasoning takes 9 ridiculous steps. Good grief, man. Every effort to point to an outside actor, like the DPRK, feels diametrically opposed to Occam’s Razor. Grasping at straws is a more apt description in my mind. Wanna hear my version of Occam’s Razor? Step 1: Sony has a massive layoff angering employees. Step 2: Angry fired employees hook up with hacker organizations and presto! Wow, see what Occam’s Razor can do when used properly?
2. You inexplicably claim that did not name any particular organization in your report. Well, hiding behind terms like “A Nation state” only fools the most simple-minded. Since you are keen on brow beating your audience with fancy terms like lex parsimoniae, let me return the favor. You can fool some of the people some of the time, but you can’t fool all of us all of the time.
Pingback: New Clues In Sony Hack Point To Insiders, Away from DPRK | vyagers
Pingback: Hack Sony, si valuta il coinvolgimento di alcuni ex dipendenti – enerd.it
Pingback: | whitehatnews.com
Pingback: Norse: El hack de Sony Pictures fue perpetrado fuera de Corea del Norte - Tus Anuncios México - anuncios clasificados gratis
Pingback: Norse: El hack de Sony Pictures fue perpetrado fuera de Corea del Norte | Fravala.com - Las noticias de tecnología a tu alcance.
Pingback: Norse: el hack de Sony Pictures fue perpetrado fuera de Corea del Norte - Smart Systems
Pingback: Norse Security IDs 6, Including Ex-Employee, As Sony Hack Perpetrators * The New World
Pingback: Norse: El hack de Sony Pictures fue perpetrado fuera de Corea del Norte | Madrid Ventures
Pingback: North Korea not behind the Sony attacks? | Pied Type
Pingback: This may be best evidence yet that the Sony hack was an inside job | POPFIX - Celebrity, Tech, Sports News
Pingback: 5 – Clues in Sony Hack Point to Insiders – Official Offeryour.com Blog
Pingback: 5 – Clues in Sony Hack Point to Insiders – Exploding Ads
Pingback: » Firma de seguridad desmiente al FBI: Ataque a Sony no vino de Corea del Norte
Hey Gary, this article just debunked your entire missive you link to there. Destroyed it, actually. Might want to try selling your products with a proven hypothesis first.
Honest Rob, Thanks for your comments.
You must not be reading my threat report in detail. Not once in the report do I name any particular organization responsible for the attack, only the methods I believe were used.
As to Norse, just remember, when India suffered a terrorist attack, they hacked the wireless router of a government official to send the threatening emails, before the attack. I doubt it was a malicious insider, especially a Japanese because I’ve studied their culture. It would be like committing suicide and losing face, for life.
Please read every word of what I write in my report and please do study Occam’s razor as it could help you. If you need anything else, our team is available at support@snoopwall.com.
To be blunt, Miliefsky’s “Threat Report” is typical white paper drivel, and his VERY surface “analysis” of Japanese culture is just that. A SURFACE ANALYSIS. Ruth Benedict couldn’t have done better.
Seriously, Gary. READ. They said “Insider”, not necessarily Japanese. I *do* know Japanese culture VERY well. Don’t even go there.
/sarc
Thank you for your comments. We will consider auctioning off her original notes for the synergy lecture at a future date. Until then, if you need more support, send us an email at support@snoopwall.com.
Pingback: Norse: El hack de Sony Pictures fue perpetrado fuera de Corea del Norte | Blog Informativo de ProfesionalesPanama
“researchers started from the premise that insiders would be the best situated to carry out an attack”
You cannot start from a premise that it’s a particular actor or type of actor from the start. That’s the reverse scientific method.
John – please make sure you understand the scientific method before you make statements about it. Here’s a flowchart for kids that may help you: http://img.docstoccdn.com/thumb/orig/86144647.png
Here’s my 2-line summary:
_MAKE A HYPOTHESIS_
_TEST/CHECK IT_
You have to start with a premise to use the scientific method – that’s the hypothesis. “I hypothesize that it was perpetrated by insiders”; does some fact checking; “The facts seem to agree with my hypothesis” – Yes, that’s scientific practice.
no it isnt. its not even close. its a pig latin or bastardized version of the actual scientific process. you seem not to have read popper, period.
Pingback: Experts Say North Korea Not Behind Sony Hack -- News from Antiwar.com
Pingback: Defensive Security Podcast Episode 99 | Defensive Security Podcast
Pingback: State Dept. remains sure on DPRK involvement in Sony hack
I understand the thesis that the extortion was inconsistent with a NK hack, but I was under the impression that the information that was being published was actually not selectively leaked by the hackers but was rather being cherry picked by journalists that were going through the gigs of data. I didn’t think there were snippets being leaked by the persons responsible for the attack.
Also, this could just be a typo, but the article makes it sound like the malware was being compiled on an internal Sony server, I think what they mean to say is that an early version of the (remotely) compiled malware contained an ip address closely associated with a server that said person of interest had access to. This would be a pretty loose tie if the person was a sysadmin.
Pingback: Sony Hack: New Evidence Points to Inside Job Say Security Experts | Nagg
Pingback: Sony Hack: New Evidence Points to Inside Job Say Security Experts | Movie And Trailers
Pingback: A Bunch Of New Evidence In The Sony Hack Is Pointing Away From North Korea » University Of Frank University Of Frank
Pingback: A Bunch Of New Evidence In The Sony Hack Is Pointing Away From North Korea | [ mukeshbalani.com ]
Pingback: A Bunch Of New Evidence In The Sony Hack Is Pointing Away From North Korea | TextRelate
Pingback: A Bunch Of New Evidence In The Sony Hack Is Pointing Away From North Korea » GeoFront Capital Group
Pingback: A Bunch Of New Evidence In The Sony Hack Is Pointing Away From North Korea | Bicara Niaga
Pingback: A Bunch Of New Evidence In The Sony Hack Is Pointing Away From North Korea | Today's Top News
Pingback: A Bunch Of New Evidence In The Sony Hack Is Pointing Away From North Korea | BawlBuster
Interesting and compelling evidence… The question now is will the US squelch this news because it’s hard to apologize and simple to deny the truth? Typical actions of bullies, buffoons and corrupted folk..
Deny the truth?? What truth? Right now everything is speculation. Please read and understand before blaming the government.
This is evidence of nothing except that a sucker is born every moment.
Pingback: Sony Hack: New Evidence Points to Inside Job Say Security Experts | USA Star
Pingback: Could Sony hacking be the work of angry laid-off Sony staff? | Peace and Freedom
The Federal Blackhole of Information (FBI) fails us again just as they did with prior to 9-11, the Boston Marathon bombing, the assignation of Christopher Stevens (https://www.scribd.com/doc/198815820/ConocoPhillips-Shareholder-Proposal-2012), etc. Congress needs to cut off funding for these over-priced federal policemen who have repeatedly concealed information from the public that could save lives or uncover public corruption (https://www.scribd.com/doc/221876320/FBI-FOIA-Request-Judge-Barbara-M-G-Lynn) under the ruse of “national security”.
Pingback: Sony Hack: New Evidence Points to Inside Job Say Security Experts - Trendingnewsz.com
Pingback: Norse Corp Says Ex-Sony Employee And 5 Hackers Leaked Emails | Radar Online
Pingback: New Sony Hack Evidence Points To An American, Not North Korea
Pingback: Firm: Sony Hack Was Inside Job From Ex-Employee; RadarOnline.com Broke The Story 2 Weeks Ago | Showbiz Spy
Pingback: New Research Blames Insiders, Not North Korea, for Sony Hack | AcrossTheFader.US
Pingback: New Research Blames Insiders Not North Korea for Sony Hack | USA Press
Pingback: Sony Hack: New Evidence Points to Inside Job, Security Experts Say | News Feed
Pingback: Cyber security firm blames insiders for Sony hack - Fortune
Pingback: Coreia do Norte pode não estar envolvida no ataque à Sony - Boa Informação
Pingback: Experts Say North Korea Not Behind Sony Hack | antiwardotcom
News flash!! !
Stammberger discovers that John Wilkes Booth did not shoot Lincoln!
Pingback: Sony Hack: New Evidence Points to Inside Job, Security Experts Say | vyagers
Pingback: Jordan Meyerowitz | A Bunch Of New Evidence In The Sony Hack Is Pointing Away From North Korea
With such terrible opsec, I guarantee investigators were already looking at her. Forensics is a simple process: build a case, get a warrant, go public and make the arrest, find more evidence on seized media. Maybe trick her into revealing more information by using an informant. The most incriminating evidence is on her HDD. It’s likely encrypted, meaning investigators need to take her when it’s unlocked.
Is that likely to happen now?
This is so transparent. Stammberger isn’t interested in ensuring her prosecution. He doesn’t care that he destroyed the investigation and that she now gets the chance to cover her tracks. He’s after personal glory and publicity for his company. Or he’s a fool. In either case, neither he nor Norse deserve any respect for this.
Pingback: Sony Hack: New Evidence Points to Inside Job Say Security Experts | usa entertainment
Pingback: Expert: Fired employee may have been behind Sony hack | usa daily