
Recently, the Akamai Threat Research Team unveiled a unique distributed brute force attack campaign targeting nearly five hundred WordPress applications. What’s interesting about this campaign? It clearly demonstrates how Web attackers are becoming more sophisticated, attempting to evade security controls – specifically Web Application Firewalls (WAFs) and rate control protections.
A Short Primer to Brute-Force Attacks
Brute force Web attackers attempt to gain privileged access to a Web application by sending a very large set of login attempts, within a short period of time. Using volumetric single source of attack is easily mitigated by blacklisting.

Today’s brute force attacks are typically characterized by volumetric attacks coming from distributed IPs. In this way, if the attacker’s source IP is detected, they can still continue with the attack campaign by switching a source IP. As part of this cat-and-mouse evolution, WAFs are enhanced with several rate control measures that detect and block volumetric attacks – including those generated by distributed, yet synchronized, IPs.
“Slow and Low”: Distributing the Attack Sources and Targets
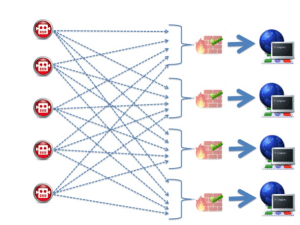
In order to slip under WAFs’ detection radars, the observed campaign leveraged a botnet whose members were not just synchronized to target a single WordPress application, but also targeted hundreds of different WordPress applications simultaneously.
The twist? Each botnet member generated just the “right” amount of traffic to evade rate control measures. Some examples:
- Over the course of an hour, each botnet member generated no more than a dozen brute force attempts to a single targeted application
- Each botnet member simultaneously targeted between 100 to 300 different WordPress applications.
- The accumulated number of brute force attempts against a single targeted application resulted in about 50 such distributed brute force attempts within an hour.
As a result, the hourly brute force rate per application that Akamai witnessed seemed low: 50 attempts.
However, given that this “slow and low” strategy enables the attacker to continue using this botnet over a long time period without being blacklisted. Operating over a few months, the attackers were able to carry out a high number of brute force attempts against that application.
That persistence pays off. At the end of the months-long campaign, the persistent and patient attacker obtains that privileged access to application.
Bypassing WAF through “Slow and Low”
Undoubtedly, a WAF protecting a single application would witness an abnormal change in the total amount of login attempts. But, as described above, each IP sends only a few requests per hour to that application. Such a small rate of failed attempts by a single IP cannot unequivocally indicate an attack by that IP. For example, the failed attempts could have been by a user who unknowingly used the Caps Lock on their machine. As another example, consider a shared IP (such as a router using NAT – or network address translation) with hundreds of users residing behind it.
The targeted application will see only a small percentage of failed attempts out of hundreds of login requests. A WAF protecting that application would refrain from blocking that shared IP address so as not to deny all that seemingly legitimate traffic.
Mitigating Low and Slow Brute Force Attacks
If we were able to look at all traffic coming from each IP to various destinations, we would be able to recognize that the attacking IPs are behaving abnormally, generating a lot of suspicious traffic. This turns out to be the key to mitigating low and slow attacks.
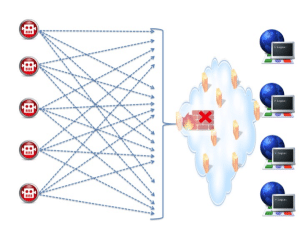
In short: it is no longer enough to just recognize the behavior of the application and identify attacks according to certain attack patterns and rates. Today’s WAFs need to view the “big picture” of network traffic against hundreds of distributed applications. That means understanding the behavior of attackers, rather than just parsing the traffic to a single application. Viewing traffic in a holistic way allows us to recognize a distributed brute force activity against multiple applications.
Taking it one step further: the monitored traffic can be correlated to identify specific bots that, collectively, make up the botnet and blacklist them. It makes sense, then, that a WAF handling such challenging threats should be enriched with threat intelligence systems (such as IP reputation) that has broad visibility over the threat landscape and can detect even elusive malicious agents. Figure 2: Mitigating “Slow & Low” attacks through a single WAF (such as a Cloud WAF) which protects hundreds of distributed applications.

Would like to understand more about slow & low attack strategy adopted recently by attackers to exploit application behind WAF.
The basic concept of this attack strategy is to use virtual distributed computing resources in order to evade security filters volumetric detection while keep the same attack magnitude.
The availability and cost of virtual computing resources makes this technique usable allowing malicious actors to execute attack campaigns and remains undetected.
Thanks for the comment, Or!