The Department of Homeland Security warned firms in the energy sector about new, targeted malware infecting industrial control systems and stealing data.

DHS’s ICS CERT, the Industrial Control Systems Computer Emergency Response Team, said it is analyzing malware associated with an ICS-focused malware campaign. The malicious software, dubbed “Havex” that was being spread by way of phishing emails and so-called “watering hole” attacks that involved compromises of ICS vendor web sites.
DHS was alerted to the attacks by researchers at the security firms Symantec (which dubbed the malware campaign “Dragonfly”) and F-Secure (“Havex”) -a remote access trojan (or RAT) that also acts as an installer (or “downloader”) – fetching other malicious applications to perform specific tasks on compromised networks. One of those additional payloads is a Trojan Horse program dubbed Karagany (by Symantec) that has been liked to prior attacks on energy firms.
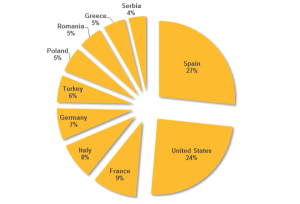
According to Symantec, the malware targeted energy grid operators, major electricity generation firms, petroleum pipeline operators, and energy industry industrial equipment providers. Most of the victims were located in the United States, Spain, France, Italy, Germany, Turkey, and Poland, the company said.
Symantec described the group behind the Dragonfly/Havex malware as “well resourced, with a range of malware tools at its disposal.”
According to F-Secure, the individuals behind the Havex malware family have been active in the last year, but began focusing on energy firms in early 2014. Specifically, the group began implanting its Trojan horse software on software downloads available from industrial control system software vendors.
Companies were infected when they downloaded and installed software updates for computers running ICS equipment. “These infections not only gave the attackers a beachhead in the targeted organizations’ networks, but also gave them the means to mount sabotage operations against infected ICS computers,” Symantec wrote.
F-Secure said it gathered and analyzed 88 variants of the Havex RAT used to gain access to, and harvest data from, networks and machines of interest. This analysis included investigation of 146 command and control (C&C) servers contacted by the variants, which in turn involved tracing around 1500 IP addresses in an attempt to identify victims.
The hacks appear to be focused on doing reconnaissance on victim networks. According to an earlier ICS‑CERT analysis of one malicious Havex payload, the malware enumerated all connected network resources, such as computers or shared resources and gathered information about connected control system devices and resources within the network. The information gathered included the CLSID (a unique identifier), server name, Program ID and OPC version. OPC is a data exchange and interoperability standard used in the industrial control space. Vendor information, running state, group count, and server bandwidth were also gathered by the malware.
Energy firms have been a frequent target of sophisticated and targeted attacks in recent years. DHS noted a sharp increase in attacks across all critical infrastructure in 2013. In recent weeks, firms in the Oil and Natural Gas sector announced that there were forming an Information Sharing and Analysis Center (ISAC) to begin sharing intelligence on cyber attacks affecting the sector, as well as best practices in responding to such attacks.
The Oil and Natural Gas ISAC (OSN-ISAC) joins similar ISACs for electricity, water, financial services, defense industrial base other critical infrastructure sectors.

Pingback: Hacked Vendors Identified In Dragonfly Attack | The Security Ledger