A report from the security firm FireEye claims that hacking crews based in Iran have become more sophisticated in recent years. They are now linked to malicious software campaigns targeting western corporations and domestic actors who attempt to circumvent Internet filters put in place by the ruling regime.

The report, dubbed “Operation Saffron Rose,”(PDF) was released on Tuesday. In a blog post accompanying the research, FireEye researchers say that it has identified a group of hackers it is calling the “Ajax Security Team” that appears to have emerged out of Iranian hacker forums such as Ashiyane and Shabgard. Once limited to website defacements, the Ajax team has graduated to malware-based espionage and other techniques associated with “advanced persistent threat” (APT) style actors, FireEye said.
The researchers claim that the group has been observed using social engineering techniques to implant custom malware on victims’ computers. The group’s objectives seem to align with those of the ruling regime in Iran, but FireEye said there is also evidence that members of the group may be ‘dabbling’ in cyber crime.
FireEye and Mandiant (which FireEye acquired in January) are among the leading private-sector firms in tracking the operation of APT groups. They say the transition from ideologically motivated web site defacements to more sophisticated online actions is typical of patriotic hacking groups, and has been observed in similar groups in countries like China.
According to FireEye, the Ajax Team has been observed using traditional phishing and social engineering techniques to gain access to sensitive networks, including firms that are part of the U.S. defense industrial base (or DIB). The group created phishing web sites that spoof login pages for specific targets in the DIB, offering login pages for services such as Outlook Web Access and VPN (virtual private network) services.
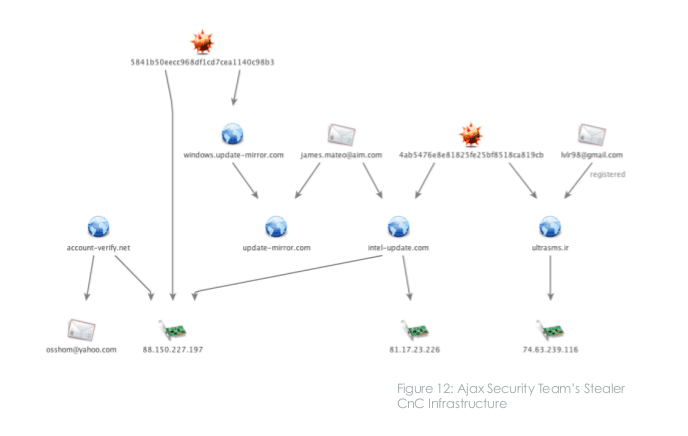
Domestically, the group targeted political dissidents, bundling a malicious program that FireEye dubbed “Stealer” with software that posed as anti-censorship tools. Online censorship is widespread in Iran, which blocks access to western sites such as Twitter and Facebook. However, many citizens still use those services with the help of anonymity tools, VPNs and proxies. FireEye said that a custom Trojan horse program, dubbed Stealer, was bundled with leading proxy applications and VPN software used in Iran. Once installed, it could grab screenshots from infected systems, harvest login credentials, web histories and snoop on other online activities.
The Saffron Rose report said that the Ajax team appears to be linked to two Iranian hackers using the handle “HUrr!c4nE!” and “Cair3x” who both became active in 2010, when they took part website defacements and participated in Iranian hacker forums such as ashiyane and shabgard. Other members include “0day”, “Mohammad PK” and “Crim3r”. Th team maintained a web site and user forums where discussions often took on a political flavor.
However, in recent months, activity associated with the group has declined and its website and forums are no longer active. It is unclear whether the group has dissolved, or merely gone underground to pursue more delicate political or cyber criminal operations.

