The security firm Akamai issued an advisory to customers on Thursday warning that a new software tool for managing distributed denial of service (DDoS) attacks was leading to a resurgence in large-scale attacks that use Simple Network Management Protocol (SNMP) traffic to overwhelm web sites.

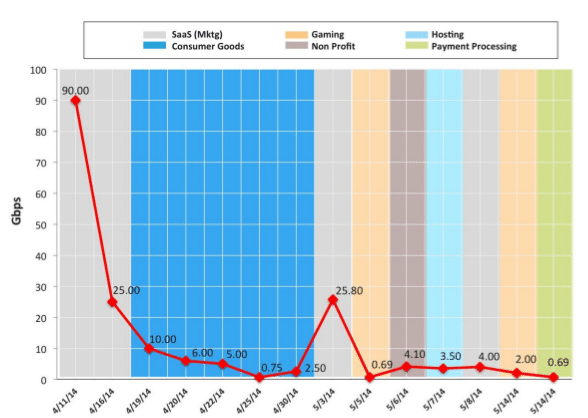
The Threat Advisory (reg wall) was issued by Akamai’s Prolexic Security Engineering and Response Team (or PLXsert). According to the advisory, Akamai began noticing a resurgence in DDoS attacks using SNMP on April 11. The company said that firms in industry verticals including consumer goods, gaming, online hosting and Software-as-a-Service and non-profits had all been targeted.
[Read more Security Ledger coverage of DDoS attacks here.]
The company has identified new- and updated tools in the cyber underground, including one dubbed SNMP Reflector – that are enabling the attacks.
Simple Network Management Protocol (SNMP) is a protocol that is used for managing devices on a network including routers, switches and network printers. It has many applications, but is commonly used to relay status and administrative messages from deployed hardware to a management console. SNMP has long been recognized as an avenue for denial of service, or “SNMP Flood” attacks.
In the latest instances, Akamai says that attackers are scanning the public Internet for devices listening on UDP port 161 and with a community string of public – basically: unsecured, Internet-connected devices that can be used as “reflectors” in the attack.
Attackers then generate snmpbulkget requests to the list of reflectors and use the IP address of the target system as the source of the request. The reflector systems respond with a flood of SNMP GetResponse data sent to the target.
The BulkGet requests are particularly useful, as they often result in an enormous volume of data being sent to the target system. In one example cited by Akamai, the GetBulk response to such a request weighed in at more than 64K, crippling the target system.
Akamai’s PLXsert said it has observed 14 such DDoS campaigns using the SNMP amplified reflection attacks since mid-April.
The company advised network administrators to upgrade to SNMP v3 when possible. Other advice to protect against the SNMP flood attacks includes limiting public access to systems on their network that use SNMP’s public community string (the default setting). Administrators should also restrict access to networked devices like printers and make sure they are not visible to- and accessible from the Internet. SNMP management devices should also be monitored closely and have restrictive access policies.