The emergence of malicious software for Google’s Android operating system has been one of the biggest security stories of the last two years. But Google is arguing that much of that reporting is hype, saying its own data shows hardly any evidence of infections of mobile devices running Android.

Speaking at the recent Virus Bulletin Conference in Berlin, Google mobile researcher Adrian Ludwig presented data that suggests the number of true infections from malicious software are vanishingly small – even in the unregulated independent Android marketplaces. But mobile security experts wonder if Google’s data isn’t burying legitimate security concerns about its mobile operating system.
The explosion of Android malware has been so well documented as to become almost a truism in the security world. McAfee in August reported a 35 percent growth in Android malware that included “SMS-stealing banking malware, fraudulent dating and entertainment apps, weaponized legitimate apps and malicious apps posing as useful tools contributed to the record increase in threats,” eweek.com reported. That included a widely reported outbreak of malware dubbed “BadNews” that masqueraded as a mobile ad network. It was found bundled with applications on Google’s official “Google Play” application store.
But Google – and Ludwig, in particular – has pushed back against such reports. Speaking at a forum in Washington D.C. in June, Ludwig argued that the search giant didn’t have any evidence linking BadNews to so-called SMS “toll fraud” malware. “We’ve observed the app(lication) and we’ve reviewed all the logs we have access to,” he said. “We haven’t seen a single instance of abusive SMS applications being downloaded as a result of BadNews,” Ludwig said – making the argument that downloads of malicious applications aren’t the same as infections from malicious software. Now Ludwig has the numbers (and the visuals) to support that argument.
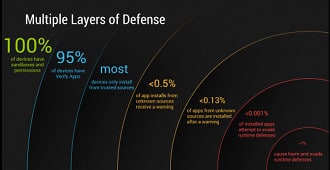
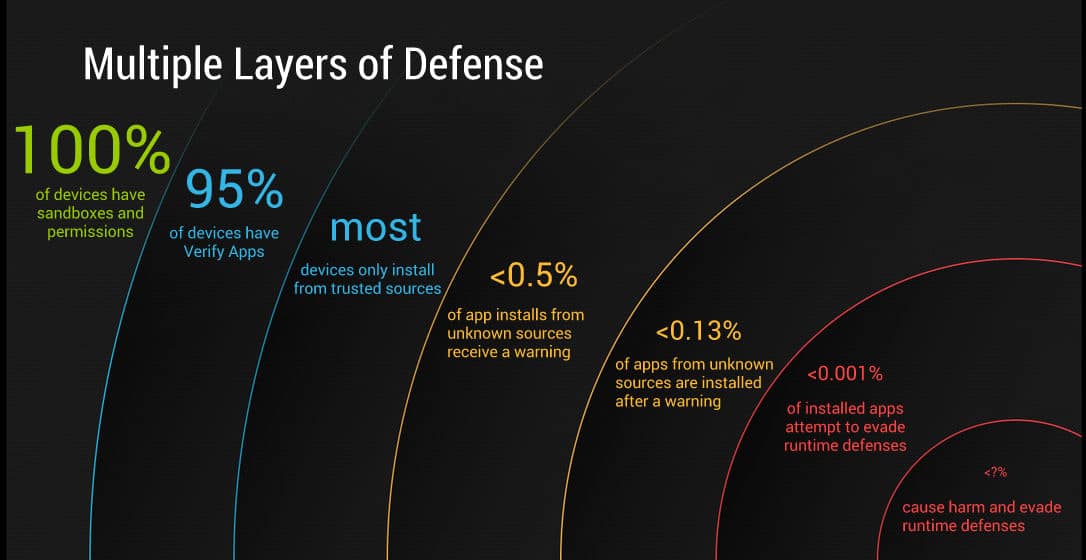
As reported by the web site qz.com, Ludwig told an audience of virus researchers and AV industry executives at Virus Bulletin that reports about Android malware (many of them propagated by AV firms) were overblown and obscured the real story: Android’s success at blocking actual infections. Citing Google data, Ludwig told the assembled that new security features, such as the Bouncer application testing service and Verify Apps technology is paying dividends.
Specifically: data collected by the Verify Apps service, which logs events involving a hazardous applications, found that only 1,200 of 1.5 billion application install attempts were incidents in which “potentially harmful applications” ended up being installed on an Android device. That’s an impressive number, but does it tell the whole story?
“Yes and no,” according to researchers at Lookout Mobile Security, which makes security software for mobile devices and first raised alarms about the BadNews malware. “Overall I agree with the trend toward fact-based information versus fear-based information,” said Jeremy Linden at Lookout Mobile Security. “In general, the number of (malware) samples is not that relevant to their prevalence or how they impact users,” he said.
Linden said that Lookout tracks the percentage of users who encounter a threat on their phone, regardless of whether the encounter results in an infection. “Just because you didn’t get infected doesn’t mean the threat is not out there,” said Mark Rogers, a principal security researcher at Lookout. For one thing, there may be mobile malware or suspicious applications that Google does not know about and, thus, is not counting.
And there are some caveats: Google can’t see many – or even most – mobile application installs that happen outside of its Google Play application store. The numbers Ludwig presented for malicious application downloads and installs on Android use a blended averaged across all the installation channels and are based on the assumption that Google’s Verify Apps technology in the loop on at least half of all installations. That’s a big assumption and could omit data from millions of devices – most outside North America and Europe – that are running customized versions of Android and/or frequenting dodgy third party application stores. True – those aren’t exactly Google’s problem, but still…
Beyond that: the experts from Lookout say couching the malicious application infection numbers, as a percentage of overall downloads diminishes the size of the problem by comparing the number to a really large number: the number of Android mobile app downloads. Had Google expressed it, instead, as a percentage of Android users would yield a larger number. Google was not able to respond to questions about Ludwig’s presentation at Virus Bulletin prior to publication of this story.
Still, neither Linden nor Rogers at Lookout challenged Ludwig’s essential claim: that installation of malicious Android apps are a relatively rare occurrence. “What we’d say is that we agree with Google’s message that ‘the sky is not falling,’ Rogers said. “While you need protection it needs to be sensible and proportional. So our position is somewhat in the middle,” he said. Security applications plus good mobile security hygiene, including safe browsing and application purchasing behaviors and a strong password to lock the device, are all prudent steps, Rogers said.