This site and others have been writing about the “Advanced Persistent Threat” problem, which has generally been treated as a euphemism for the government and military of The People’s Republic of China or – in some cases – Russia, Iran, North Korea or other un-friendlies. Firms like Mandiant have taken pains to separate the concept of APT from run of the mill cyber criminal hacking groups whose motivation is profit, rather than the acquisition of information that can be used to advance geopolitical or economic goals. Cyber criminal groups may well use “advanced” in their attack methods and “persistent” in their efforts to compromise victim networks, but they weren’t “APT.”

Now Symantec Corp. has put a fly into that ointment: publishing a report that pulls the covers off an APT group dubbed “Hidden Lynx” that it claims is responsible for some of the most sophisticated and large scale hacks of the last five years. The group compromises sophisticated and security conscious organizations and government agencies…for a price.
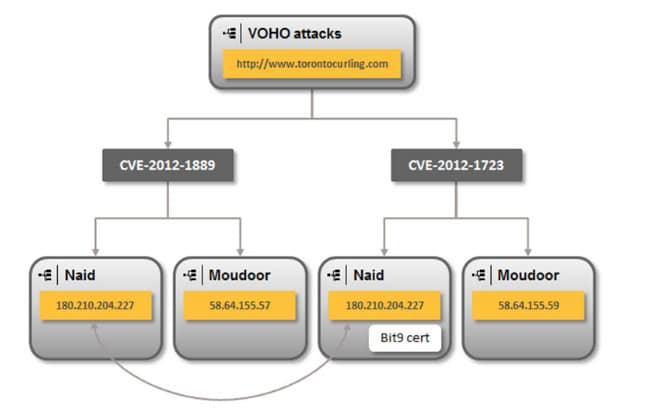
Symantec published the report on Tuesday, revealing that the Hidden Lynx group is linked to a number of prominent hacks in the last three years, including the widely covered “Aurora” attacks against Google and other organizations in 2009, the “VOHO” attacks on financial services, education and public policy web sites in 2012 and a compromise at the security firm Bit9 that resulted in malicious programs being added to that company’s “whitelist” of sanctioned applications.
The company said Lynx has been linked to attacks on both commercial and government organizations, attacking “public facing infrastructure” like web servers, often targeting popular web sites that are “watering holes” for their intended victims: employees of organizations in the public and private sector, including financial services, law, education, and local, state and federal government agencies.
According to Symantec, Hidden Lynx has been active since 2009 and employs a stable of talented hackers, malware authors and other security pros. The group’s “tactics and procedures are innovative and typically cutting-edge,” comprising “custom tools and techniques that they tailor to meet their objectives and maximize their chance of success.” In fact, Symantec claims that Hidden Lynx is far more rigorous and sophisticated in their attacks than even “APT 1,” the hacking crew detailed in a report by the security firm Mandiant in March (PDF) and believed to be synonymous with “Unit 61398,” a division of the 2nd Bureau of the People’s Liberation Army (PLA) General Staff Department’s (GSD) 3rd Department.
Among other things, Hidden Lynx is believed to be the source of two, prominent families of data-stealing trojan horse programs. One is Backdoor.Moudoor, a customized version of “Gh0st RAT”, which Symantec said is used mostly in large-scale campaigns that span industry verticals. A separate operational team within Hidden Lynx is believed to be the creator of Trojan.Naid, the Trojan used against Bit9 incident and a number of other, highly targeted attacks that were part of the VOHO campaign and “Operation Aurora” in 2009.
Unlike Unit 61398, however, Hidden Lynx appears to be motivated by profit rather than patriotism. Symantec notes that its analysis of the targets of Hidden Lynx attacks (9% of which were located in China) suggest that the group is “part of a professional organization…tasked with obtaining very specific information that could be used to gain competitive advantages at both a corporate and nation state level.”
“It is unlikely that this organization engages in processing or using the stolen information for direct financial gain. Their mode of operation would suggest that they may be a private organization of ‘hackers for hire’, who are highly skilled, experienced professionals whose services are available for those willing to pay,” Symantec said.
Check out the full report here.

